proj6
6.1 Assembler
P5 review
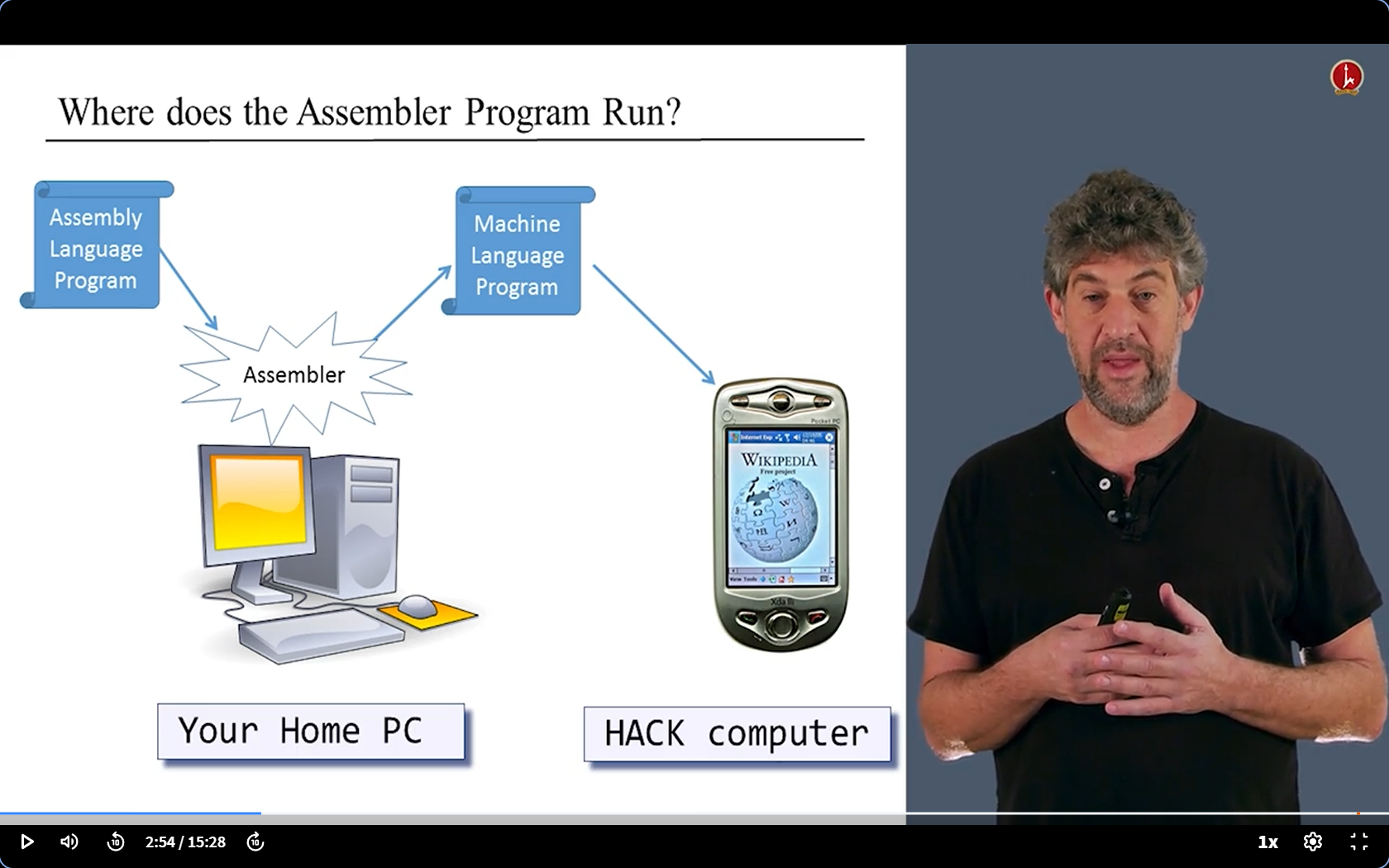
What we need: an Assembler
- 汇编器:把汇编语言,转化成机器语言的一个sofe ware(the first sofeware layer above the hard ware)
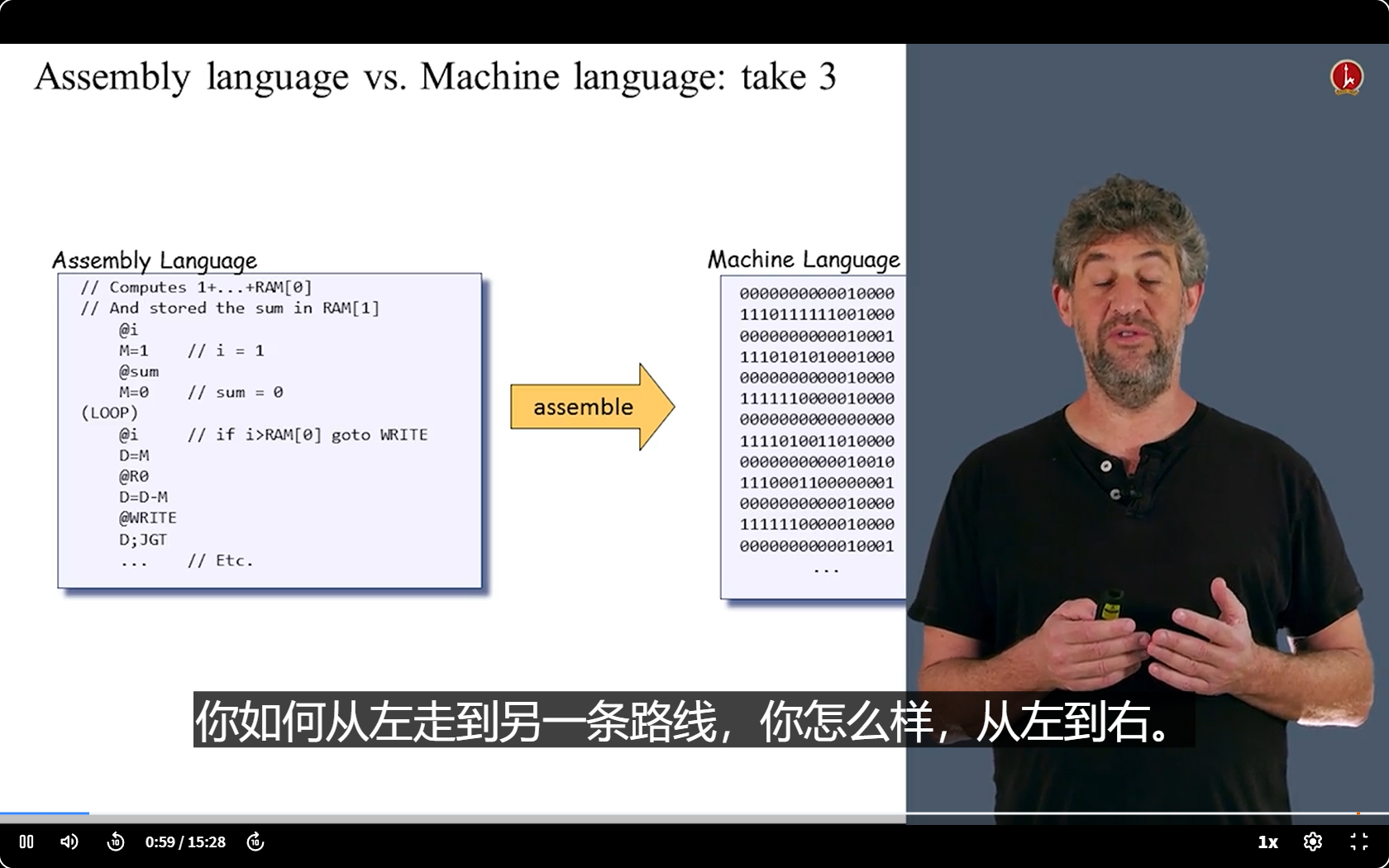
A fun way to look at Assembler
- We already have our first computer. It is difficult to write machine language.
- So we can bulid our second computer(is acutally a sofeware haha), which is called Assembler ( can translate assembly language to machine language)
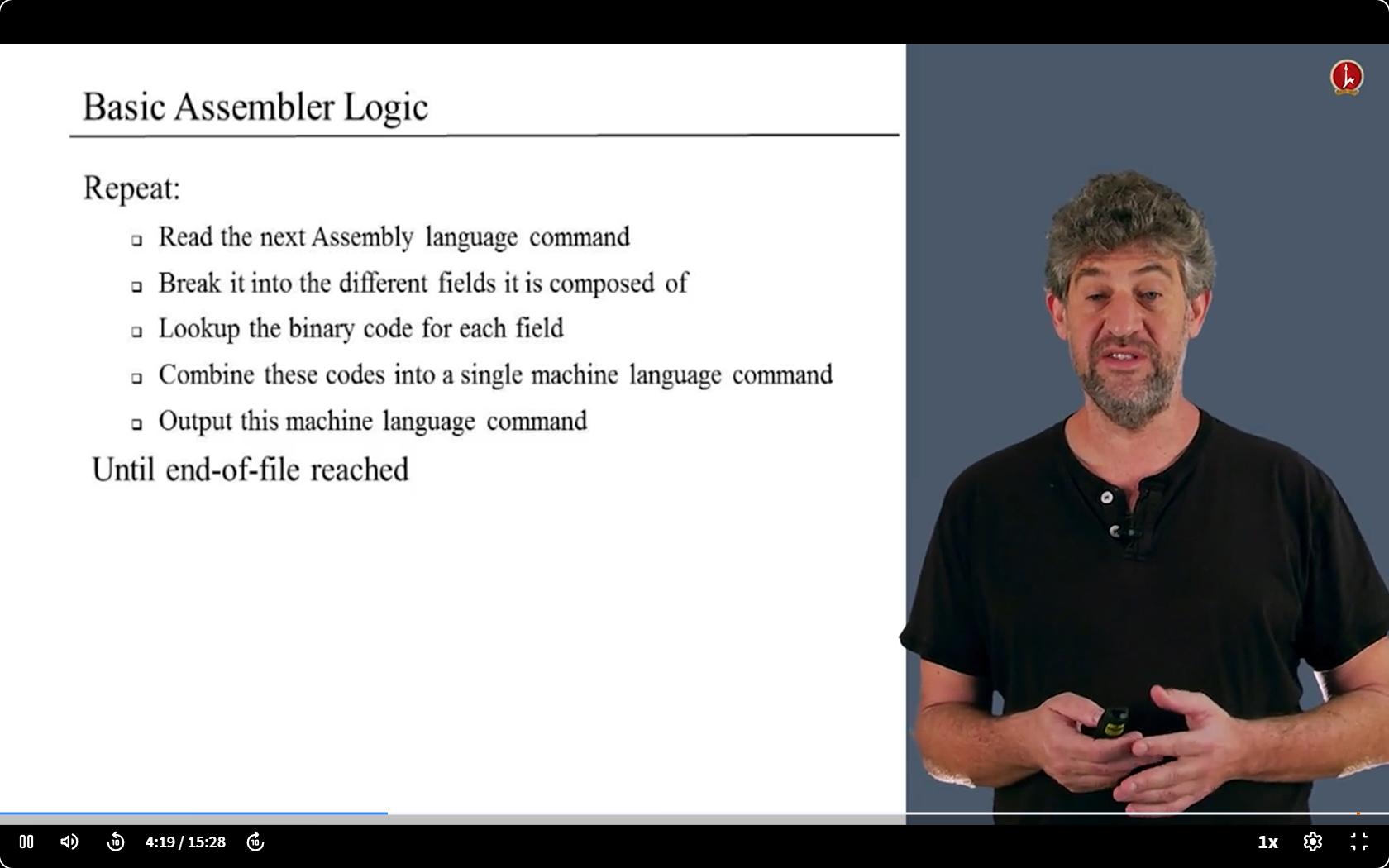
Basic Assembler Logic
basic
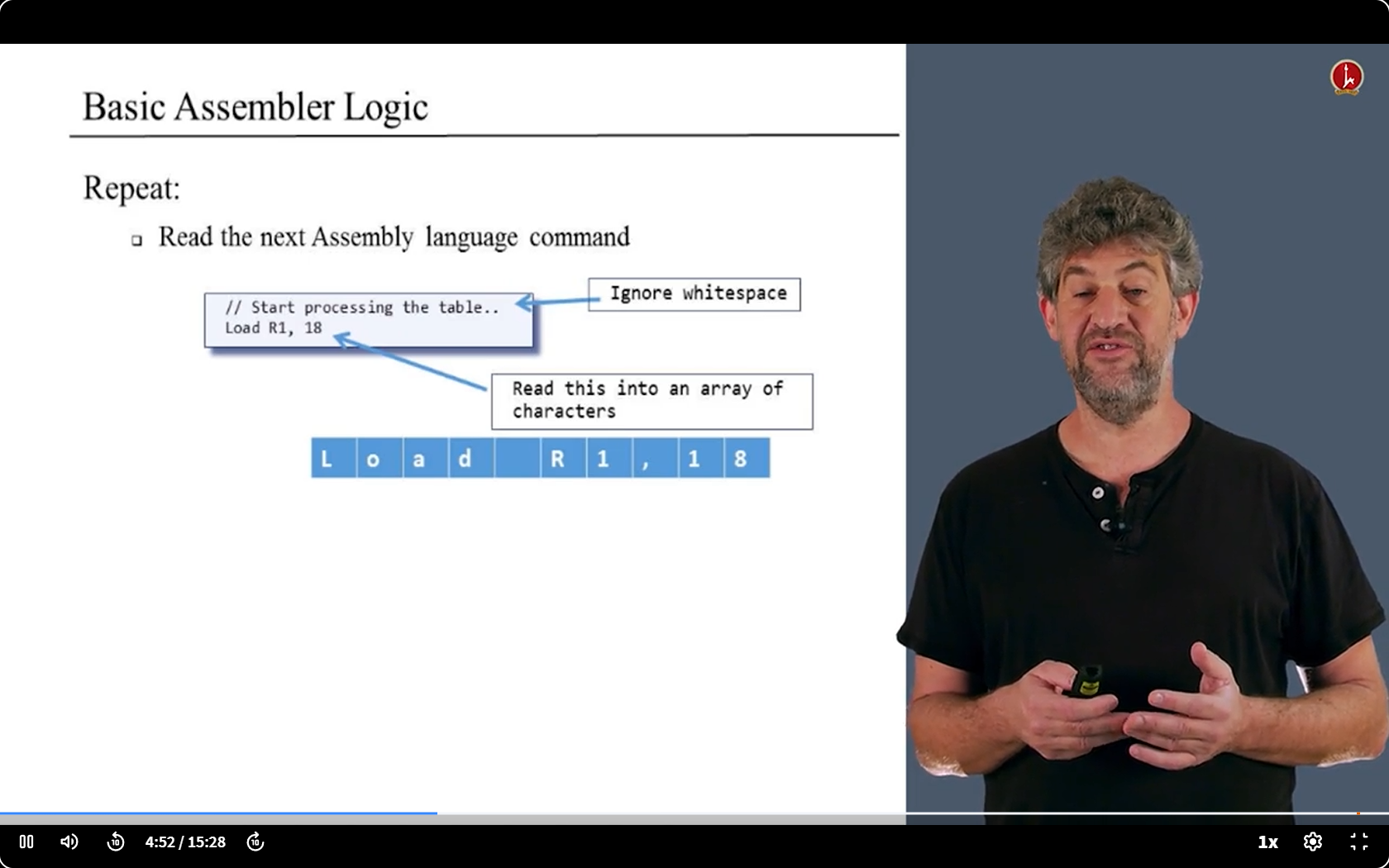
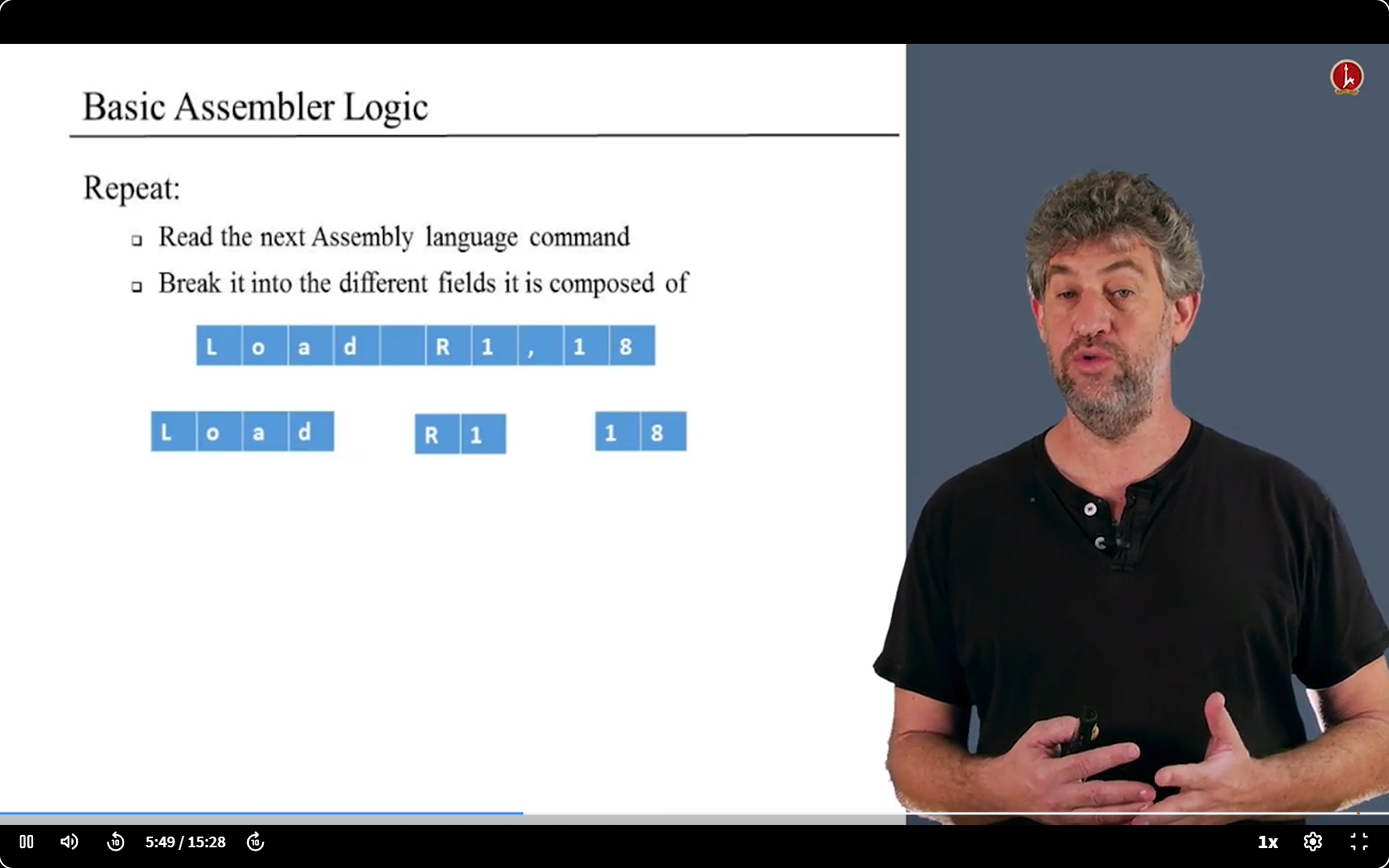
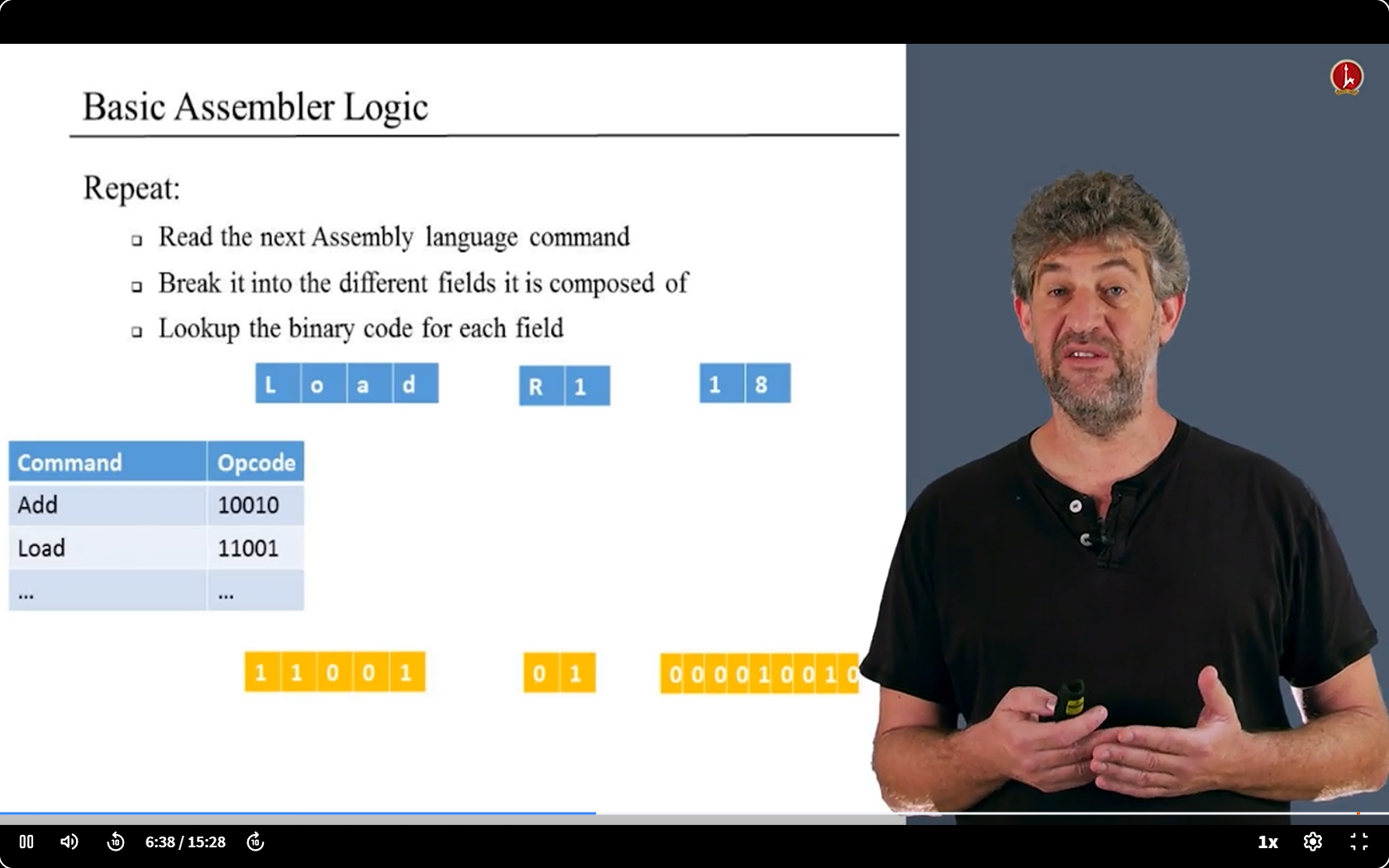
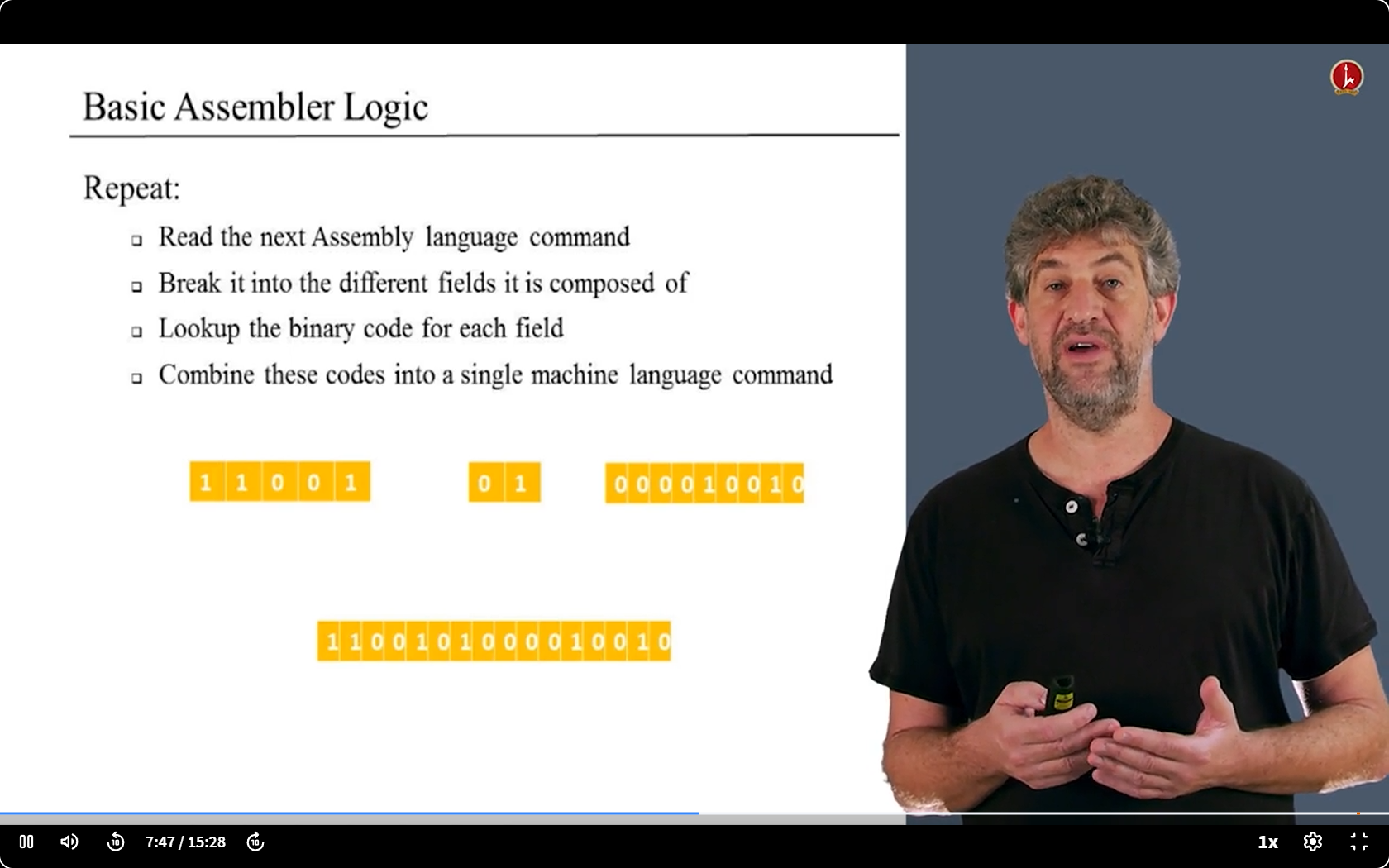
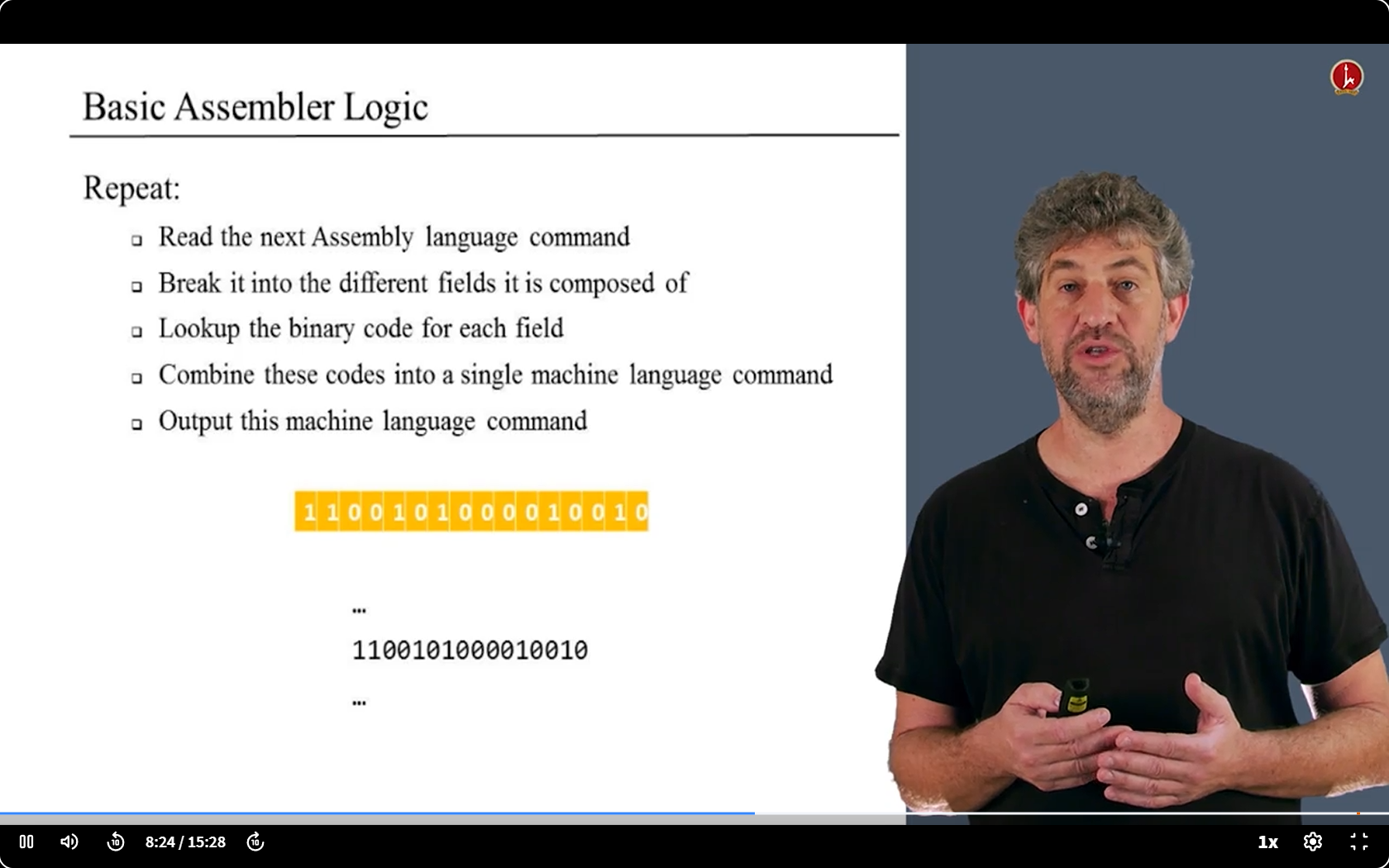
other
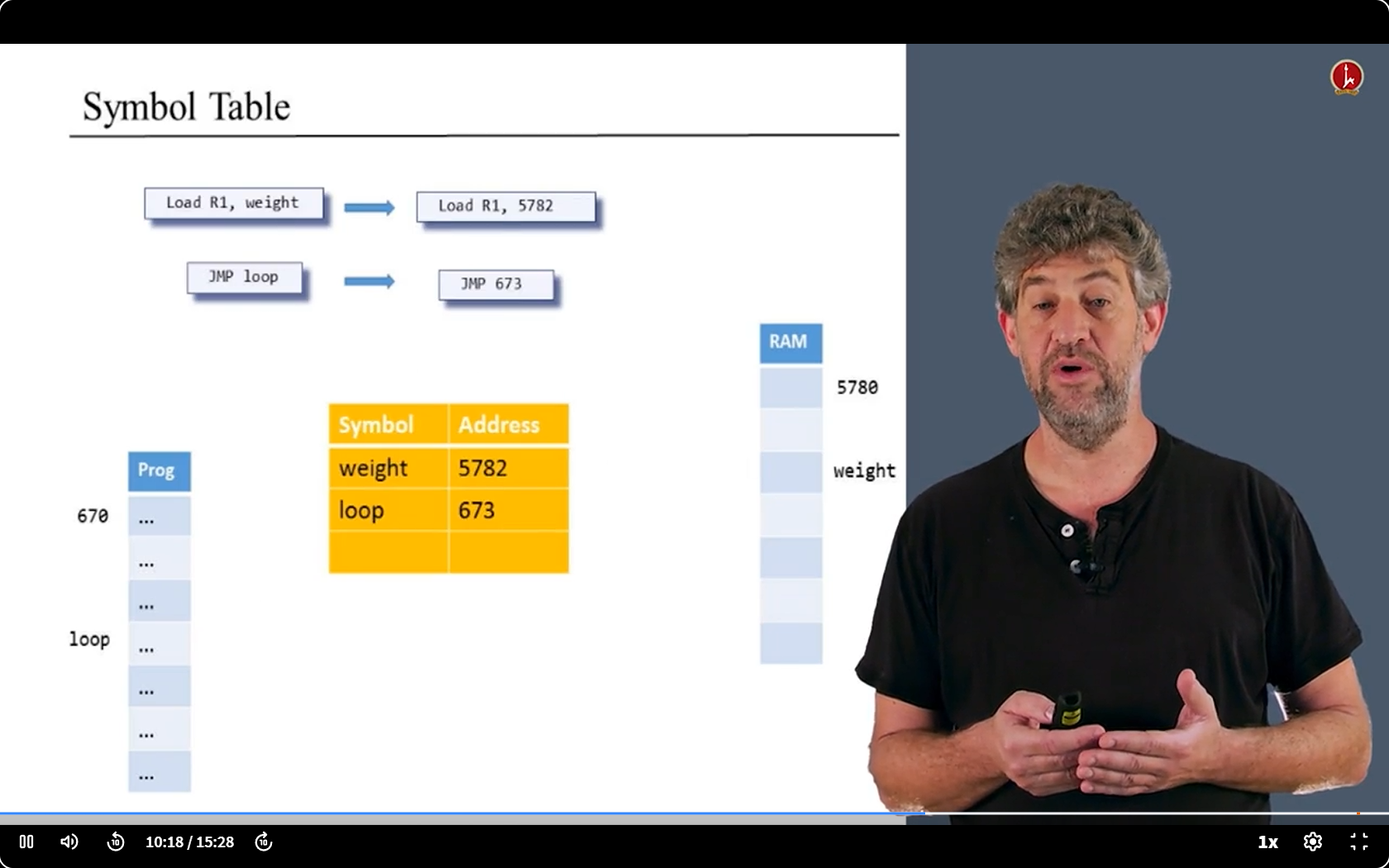
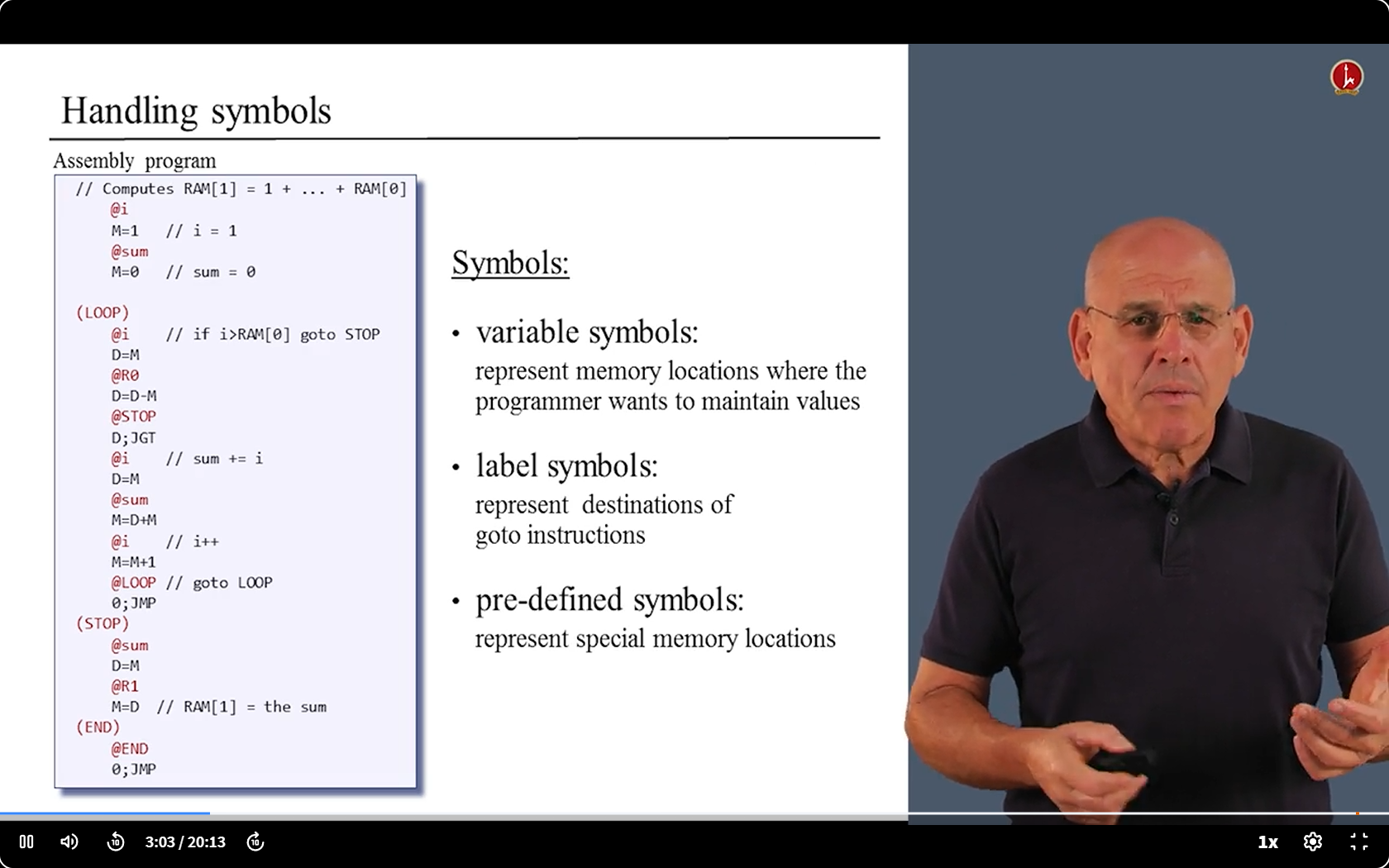
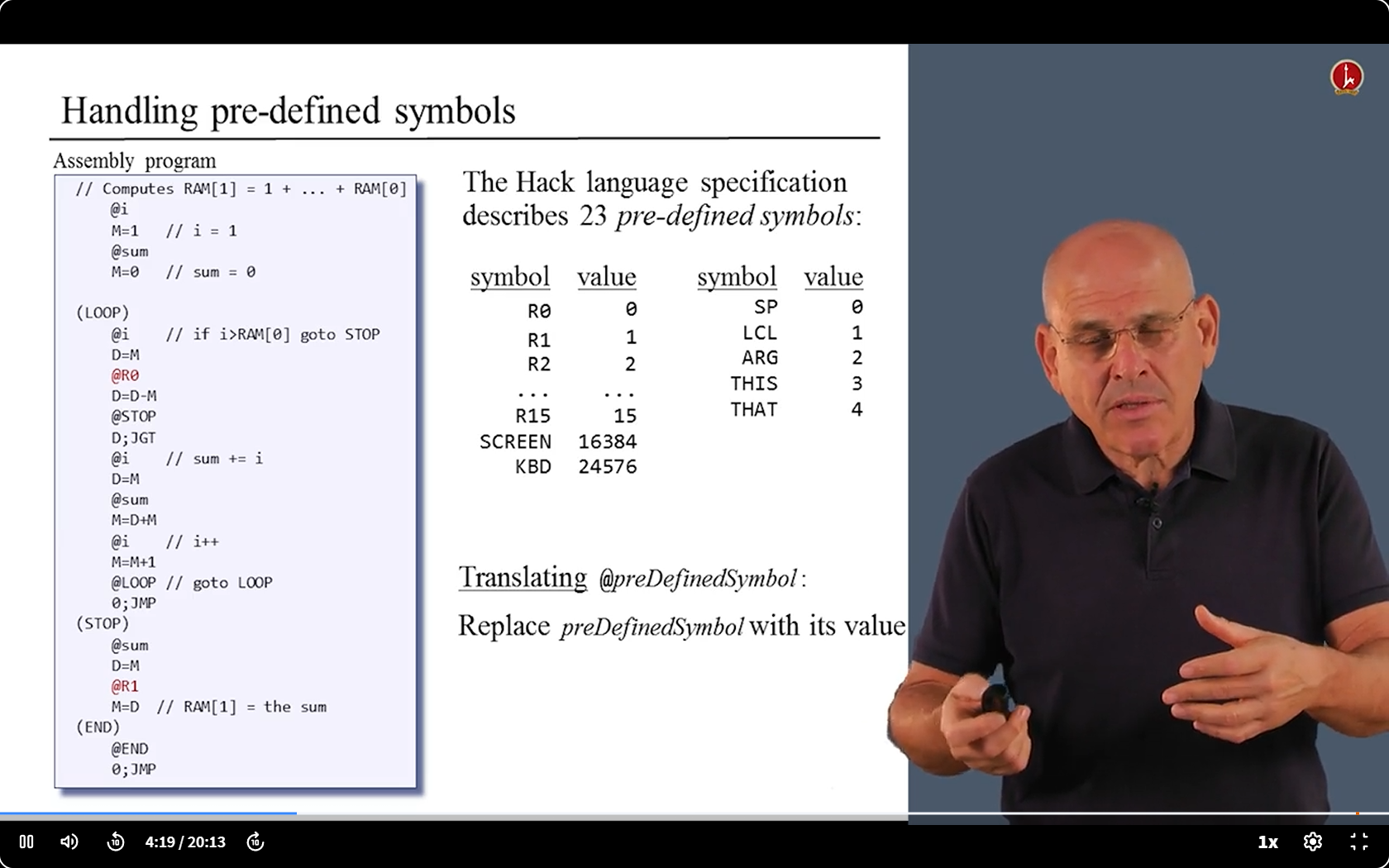
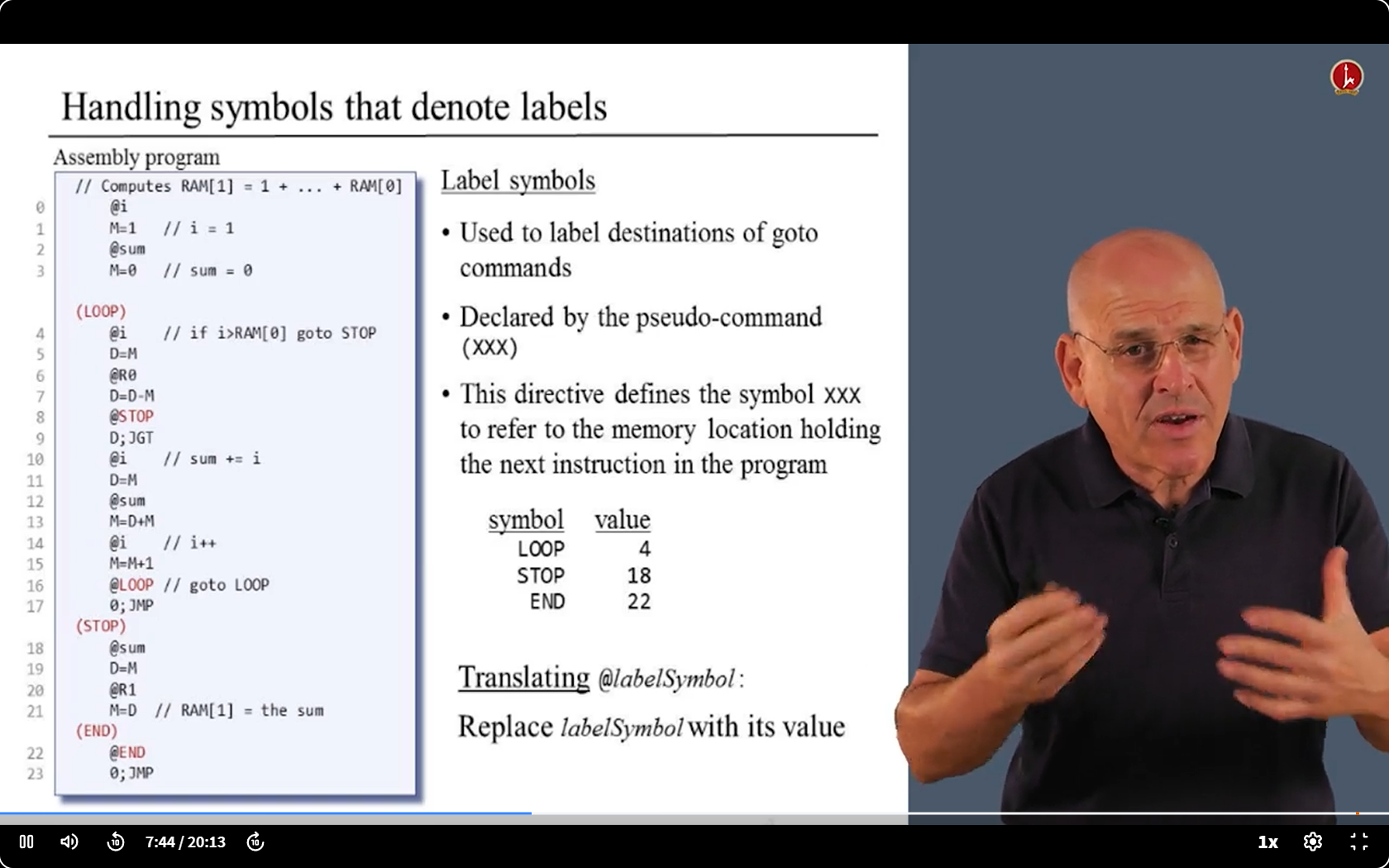
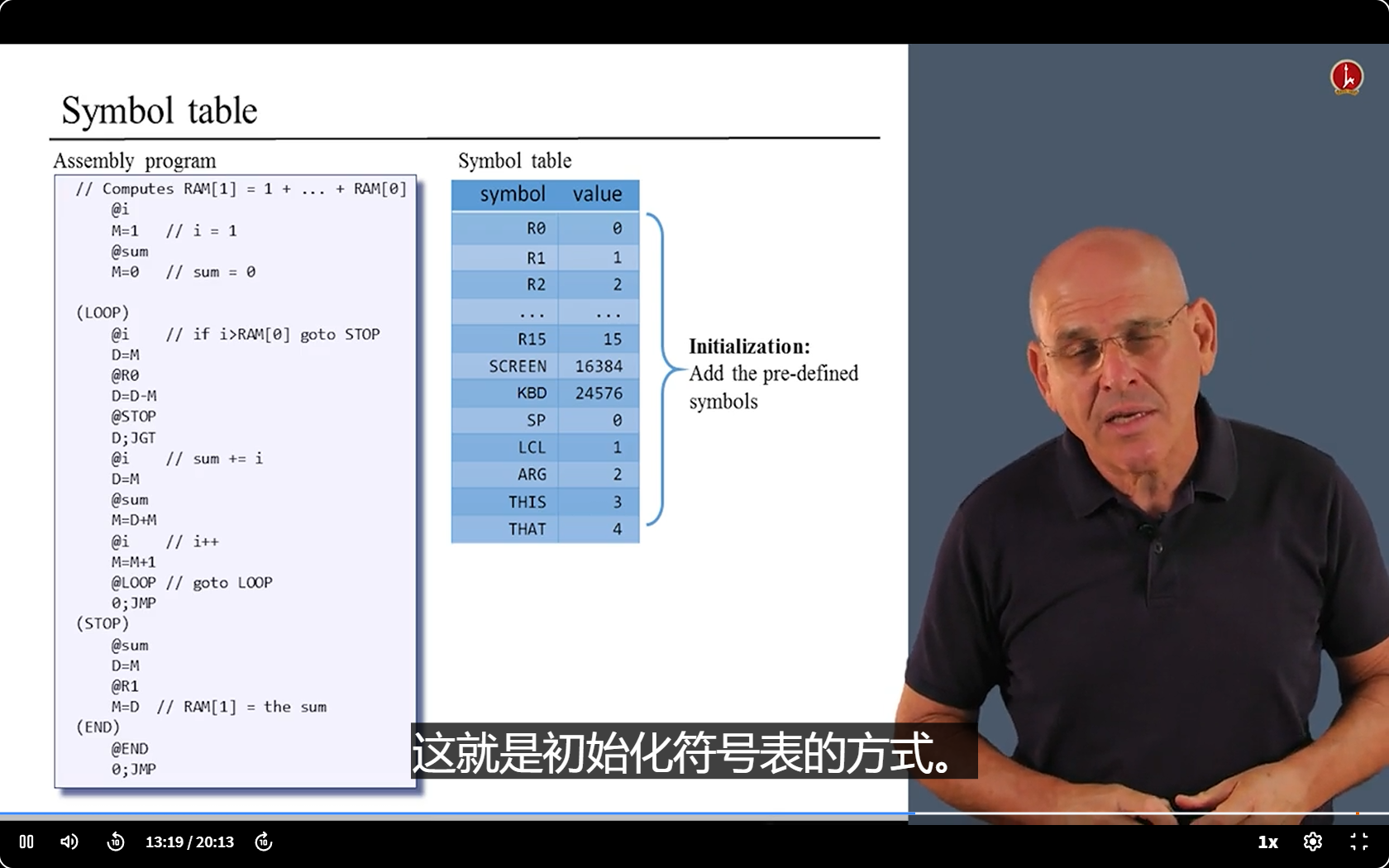
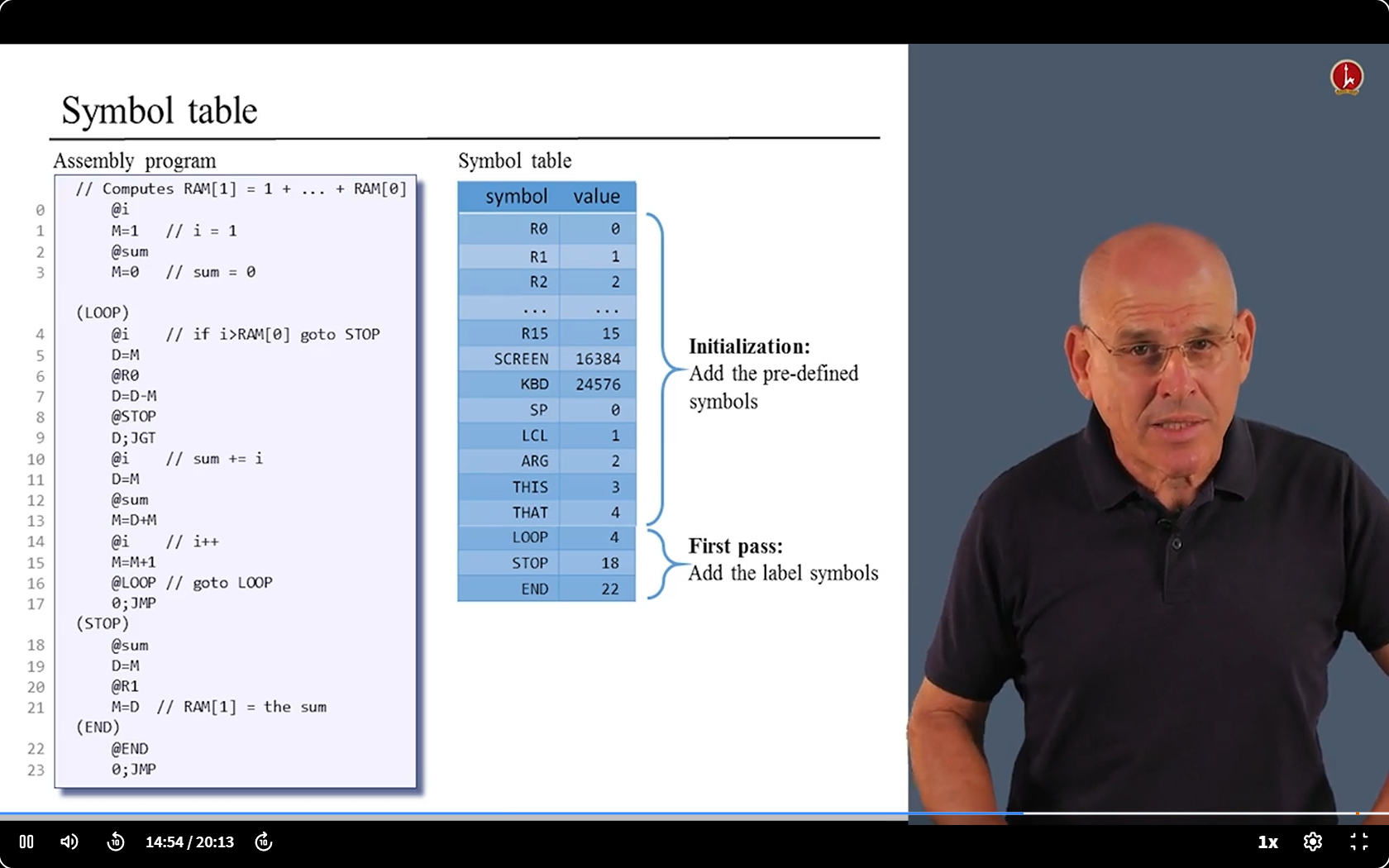
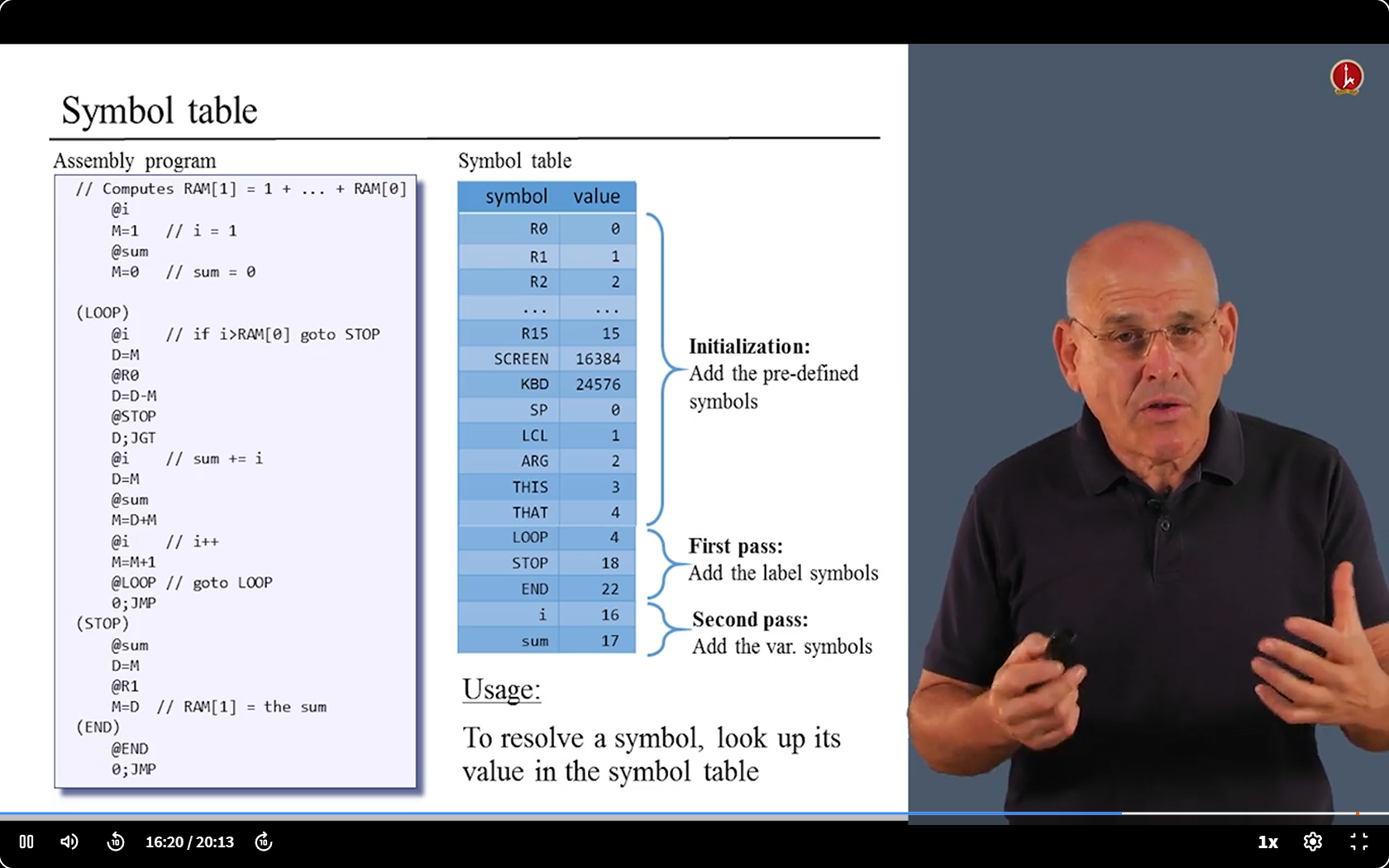
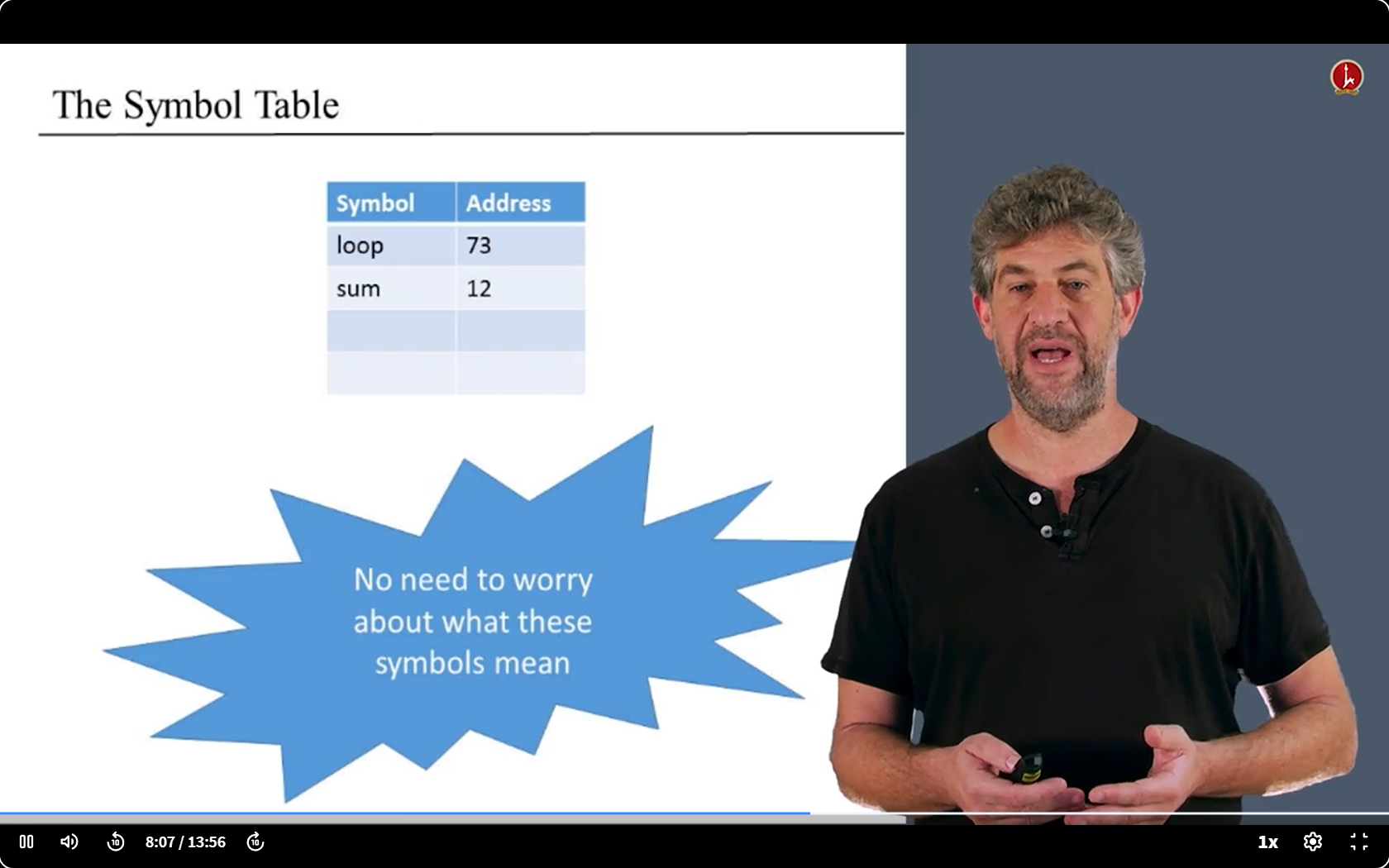
- We have something to deal with - the Symbols.
- We have two kinds of symbols: Labels and Variables.
- We need replace their names with address
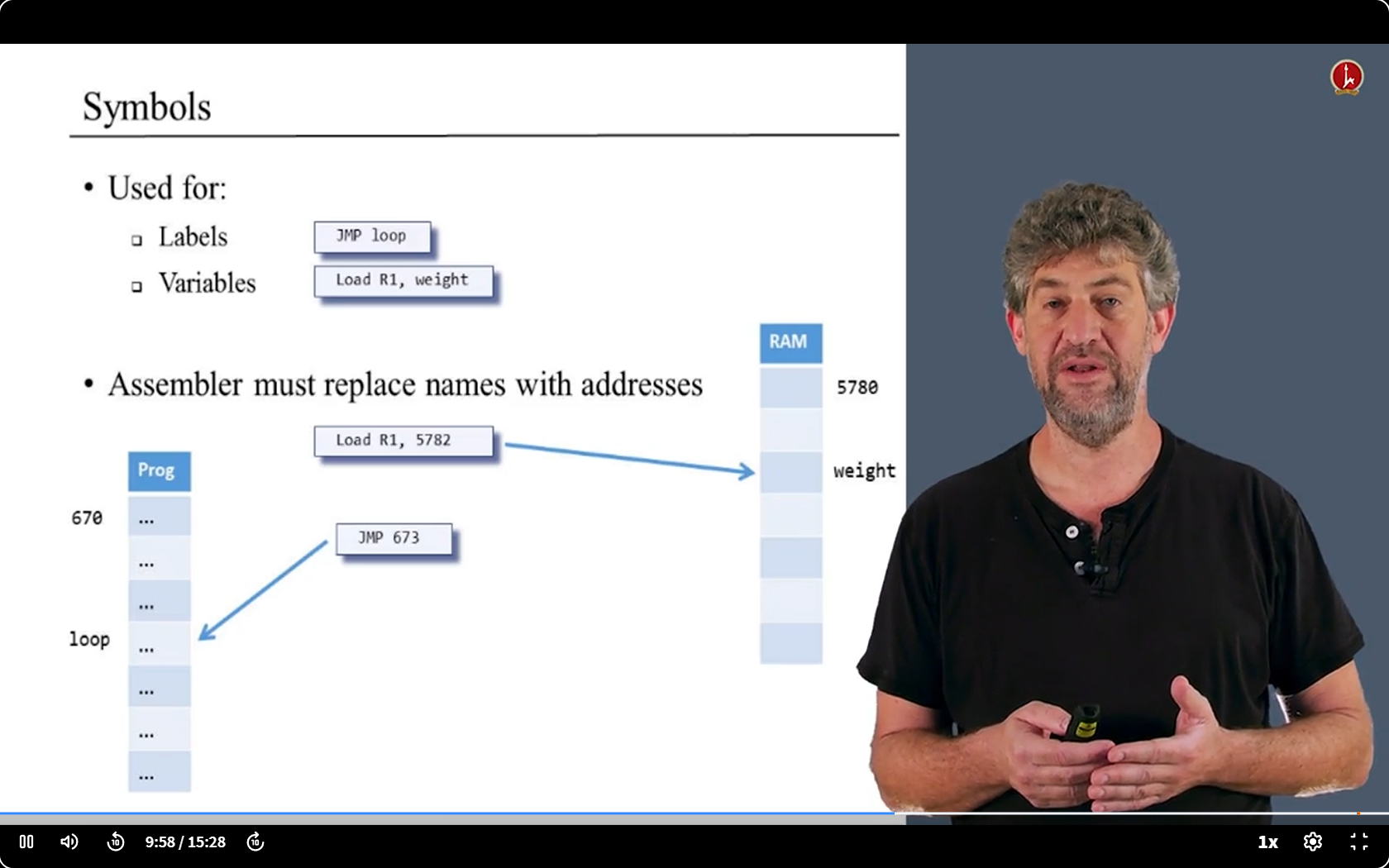
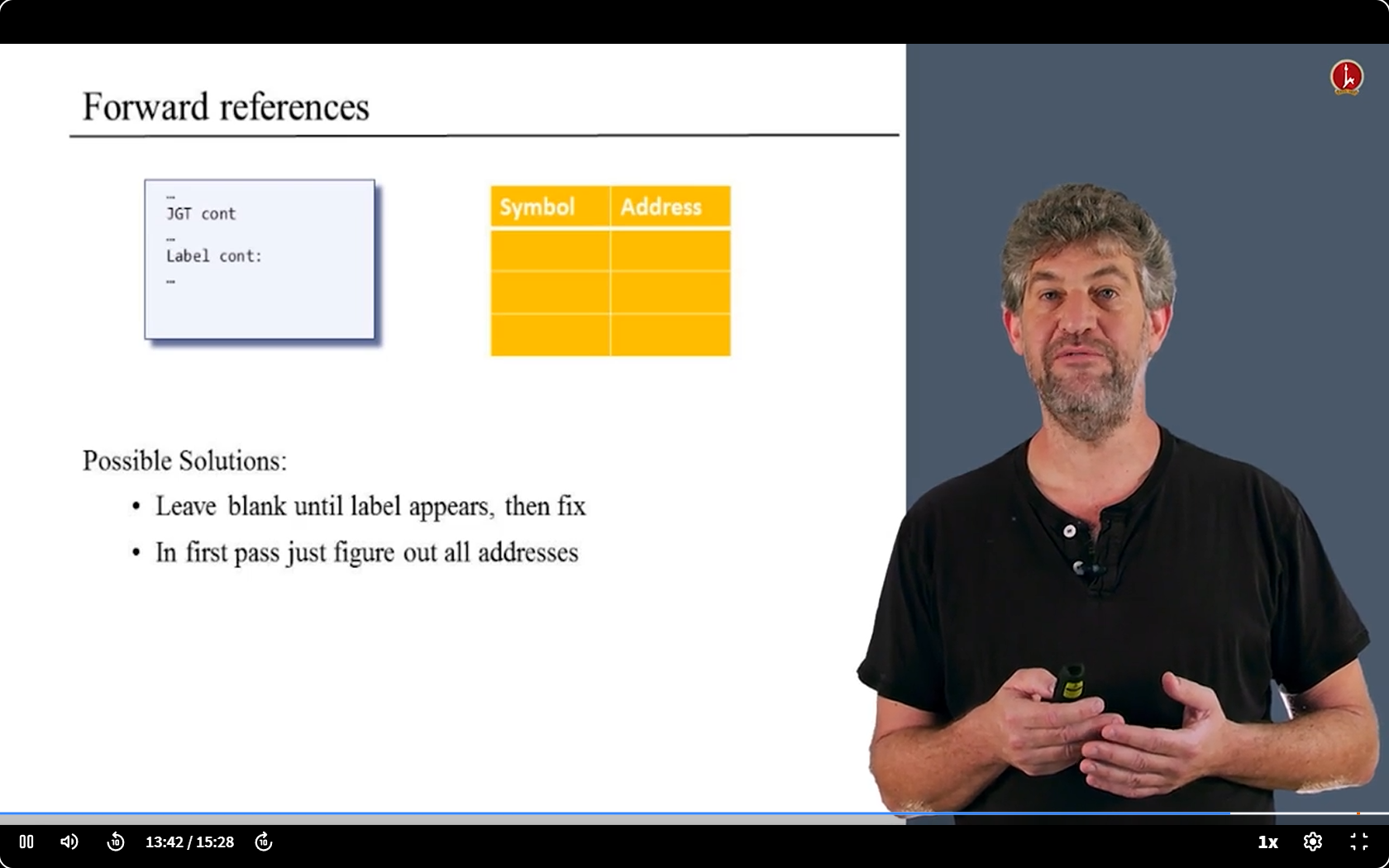
last problems
- Sometime we need the labels before we define them.
- I like the second solution.
6.2 The translator’s challenge ( preparation )
- We will soon actually build our Assembler.
- To start with, we need to know the challenges we may face.
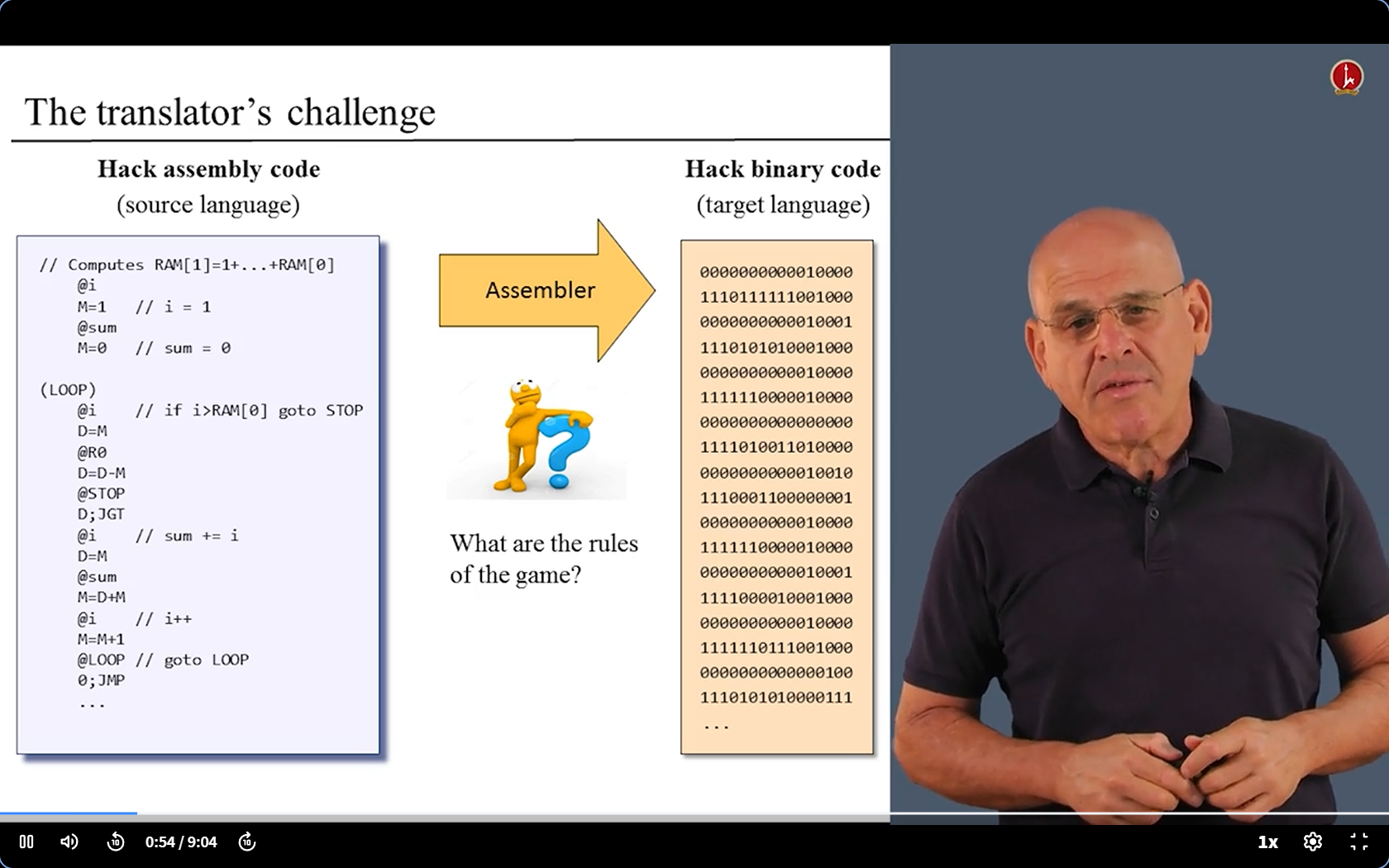
- So, we need to know the syntax of Hack language
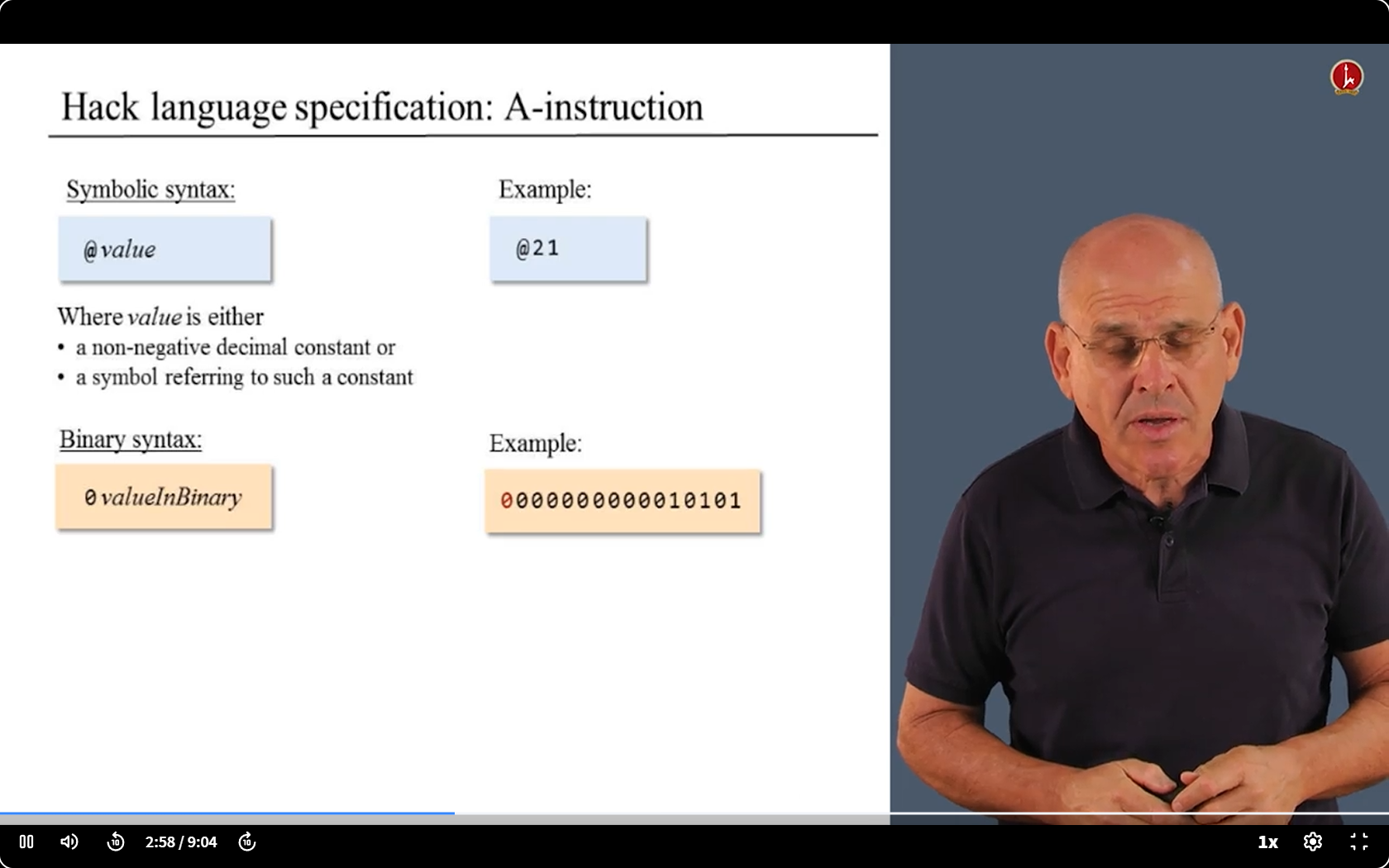
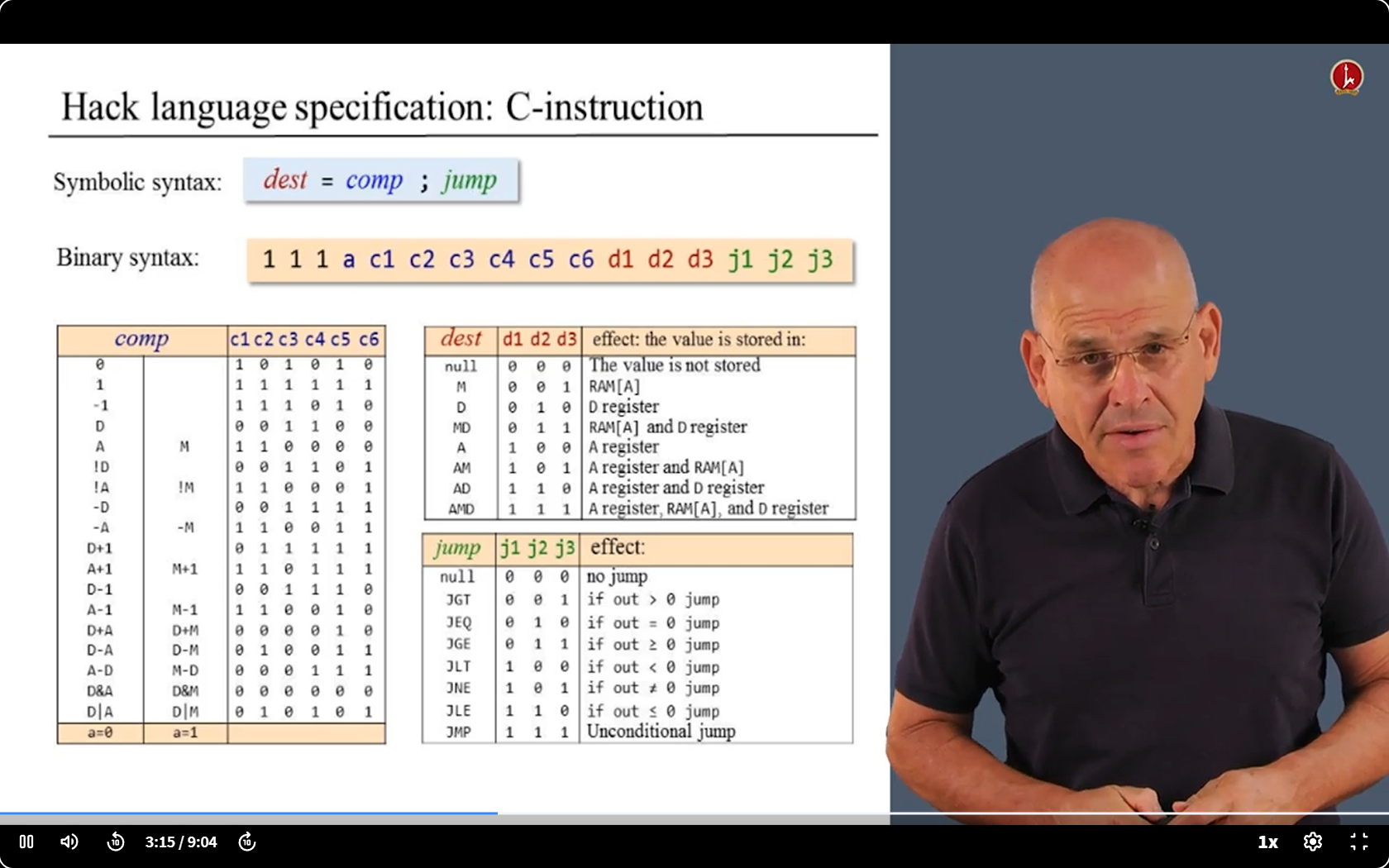
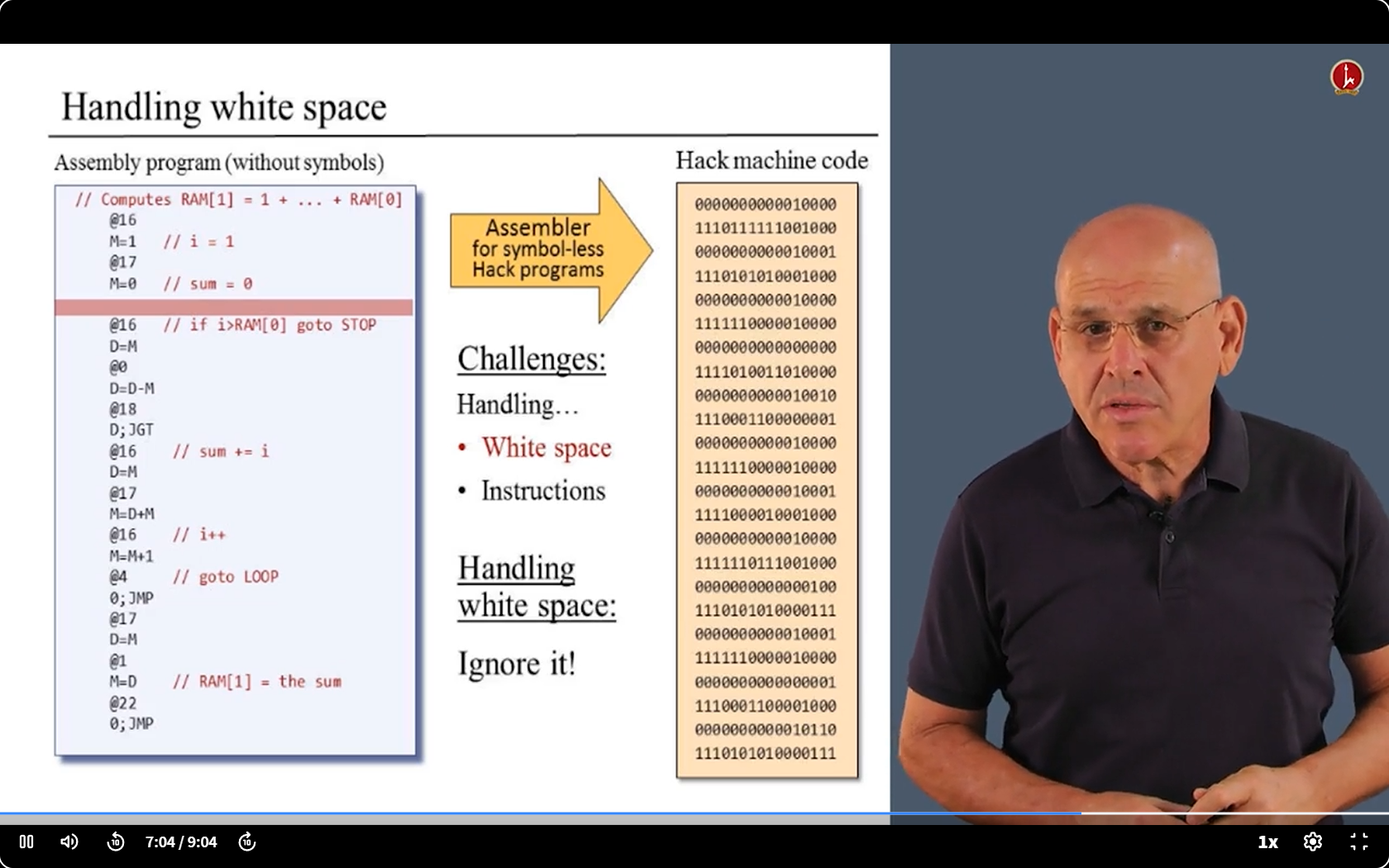
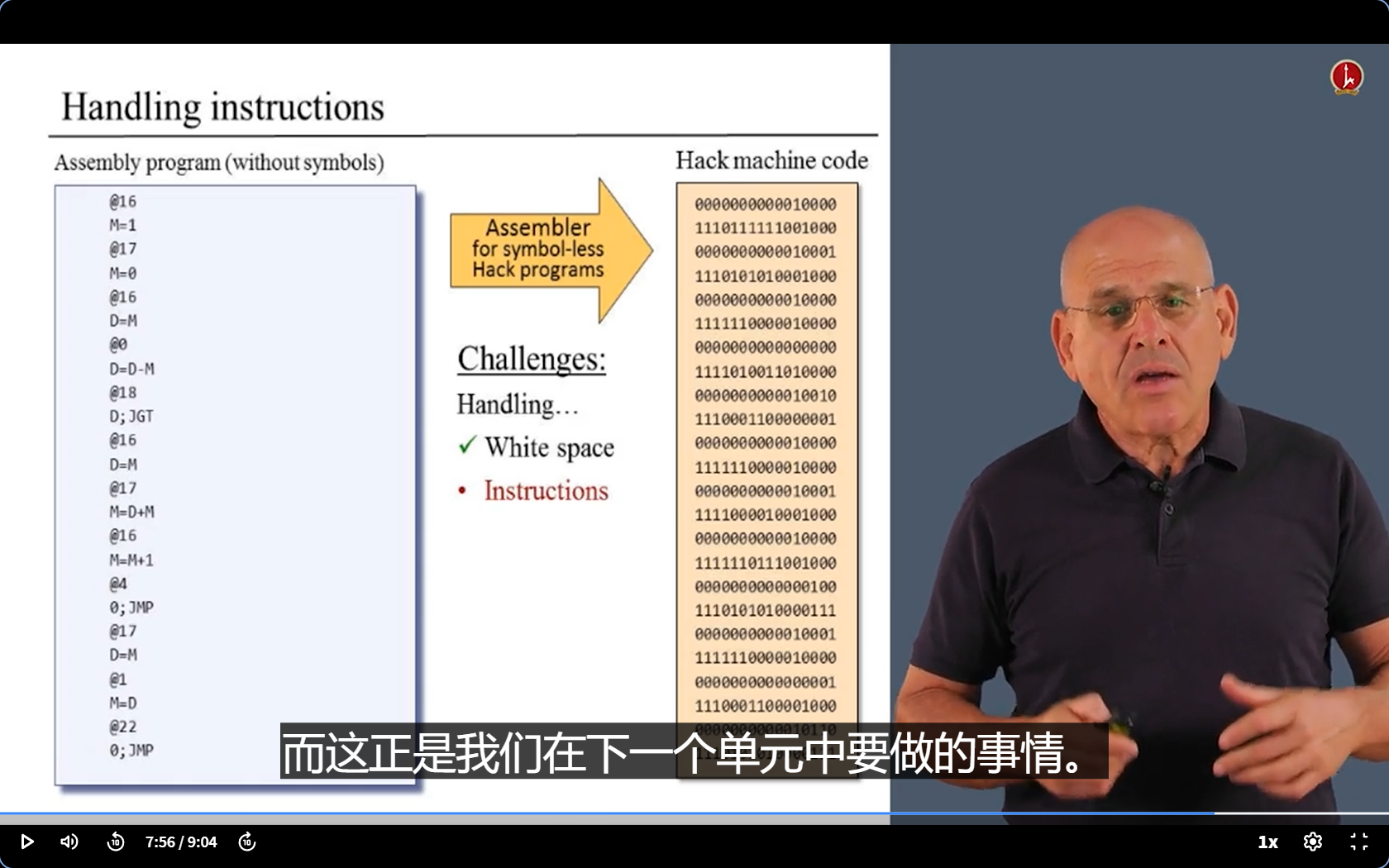
- Those are all the challenges.
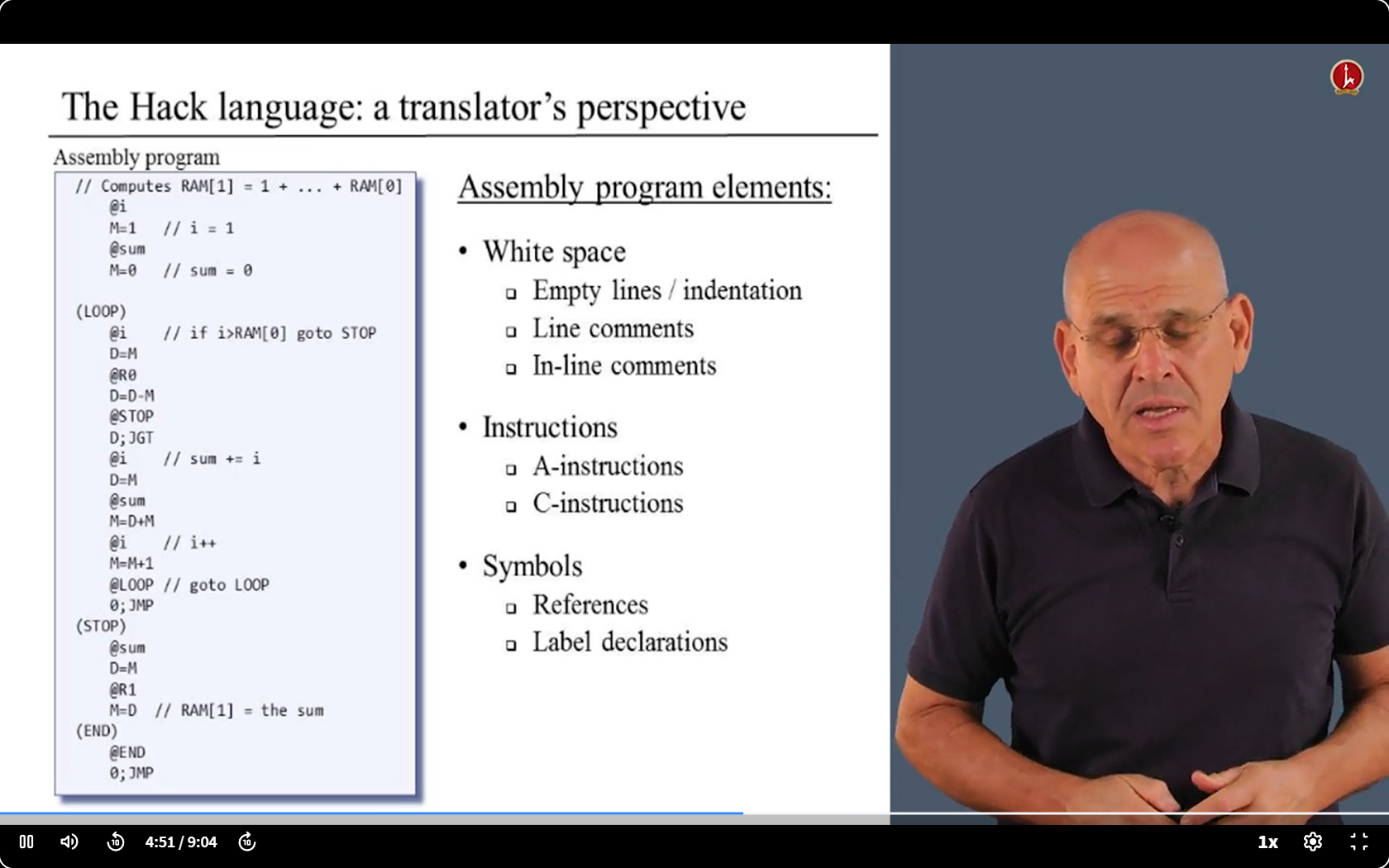
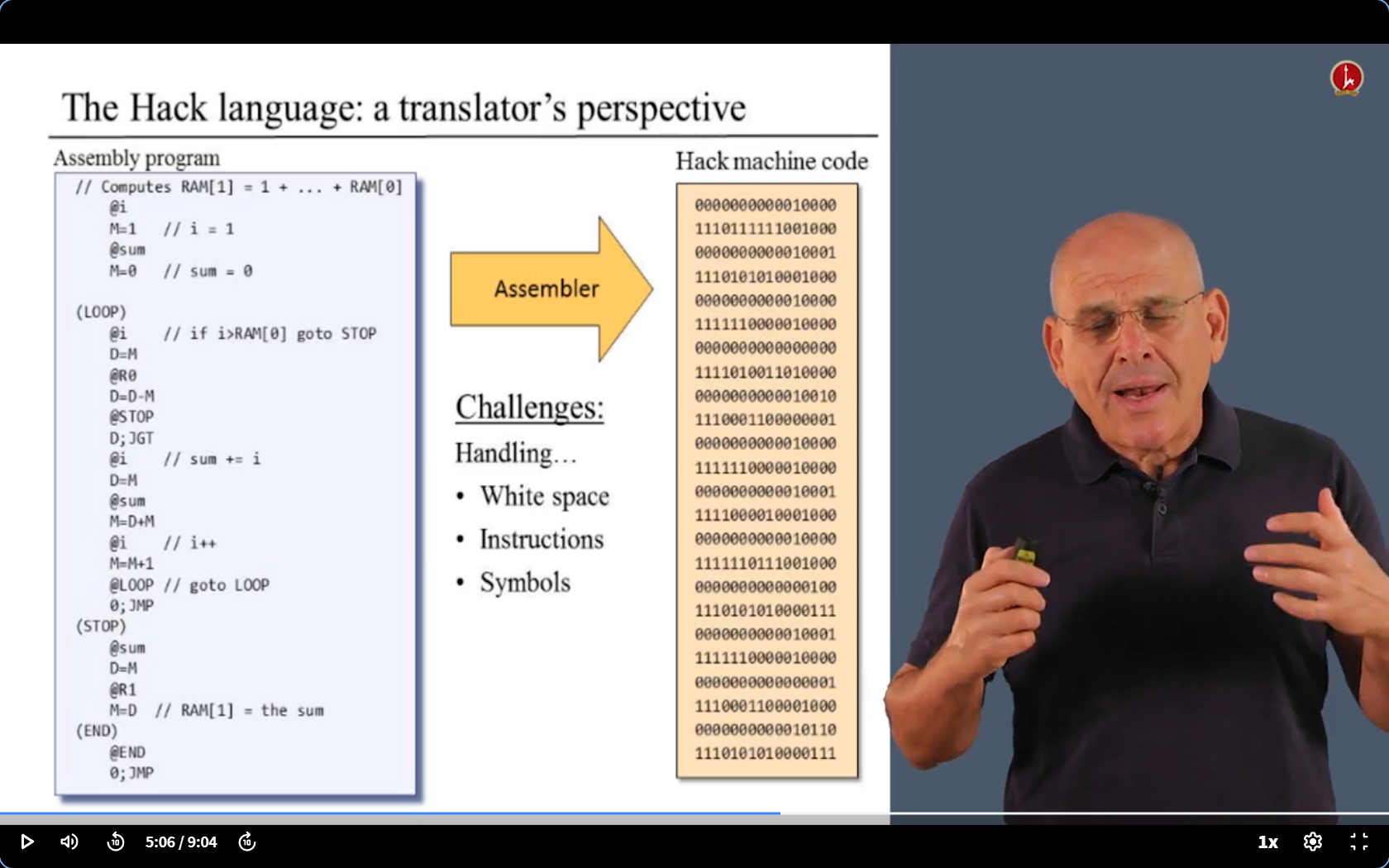
- Let’s deal with them one by one.
- Symbols are difficult, so we will deal with them later. ( Summiting the mountain may be easier from the other side than from the starting side. )
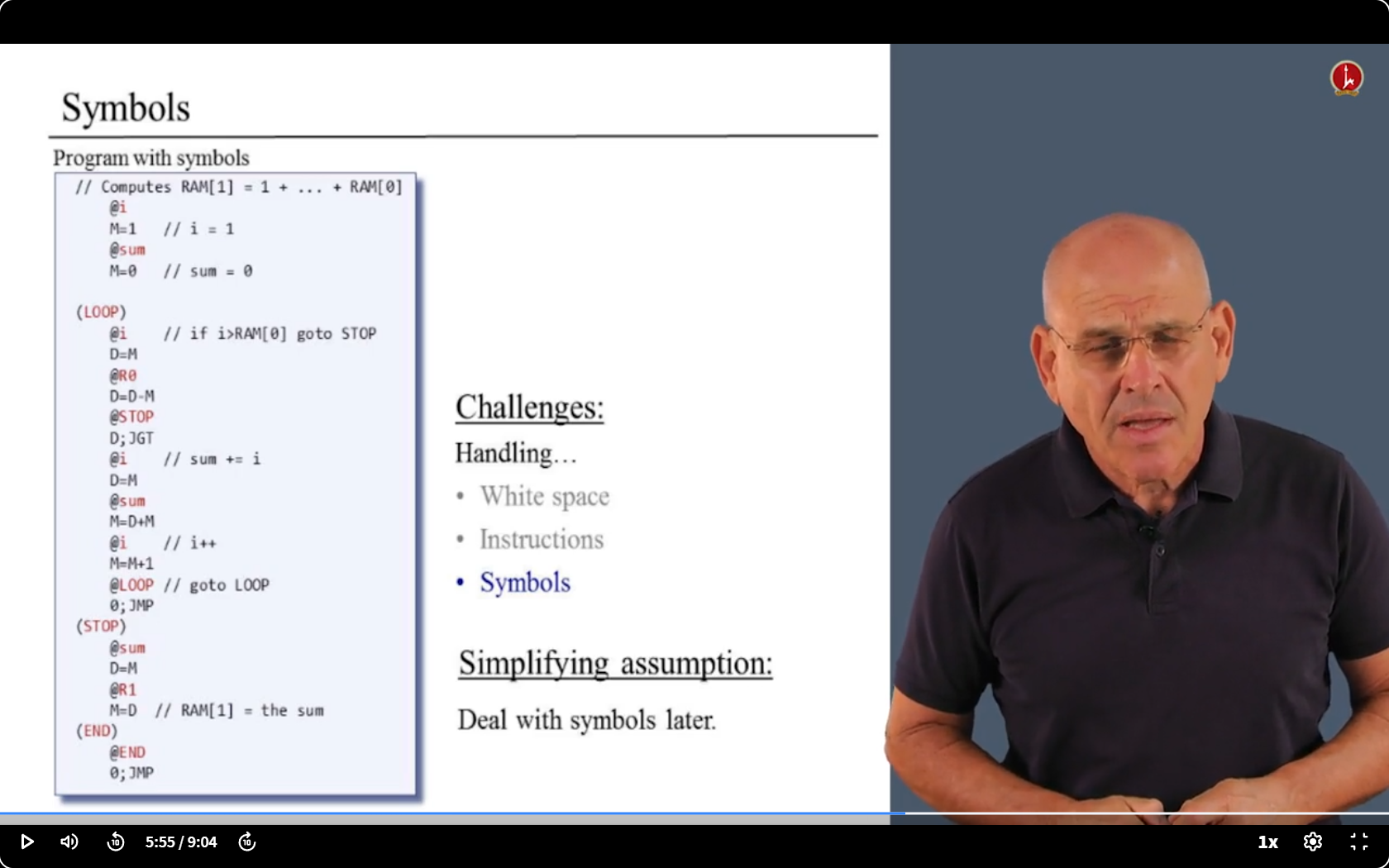
- The plan ahead

6.3 Translating challenge 1 : A/C Struction
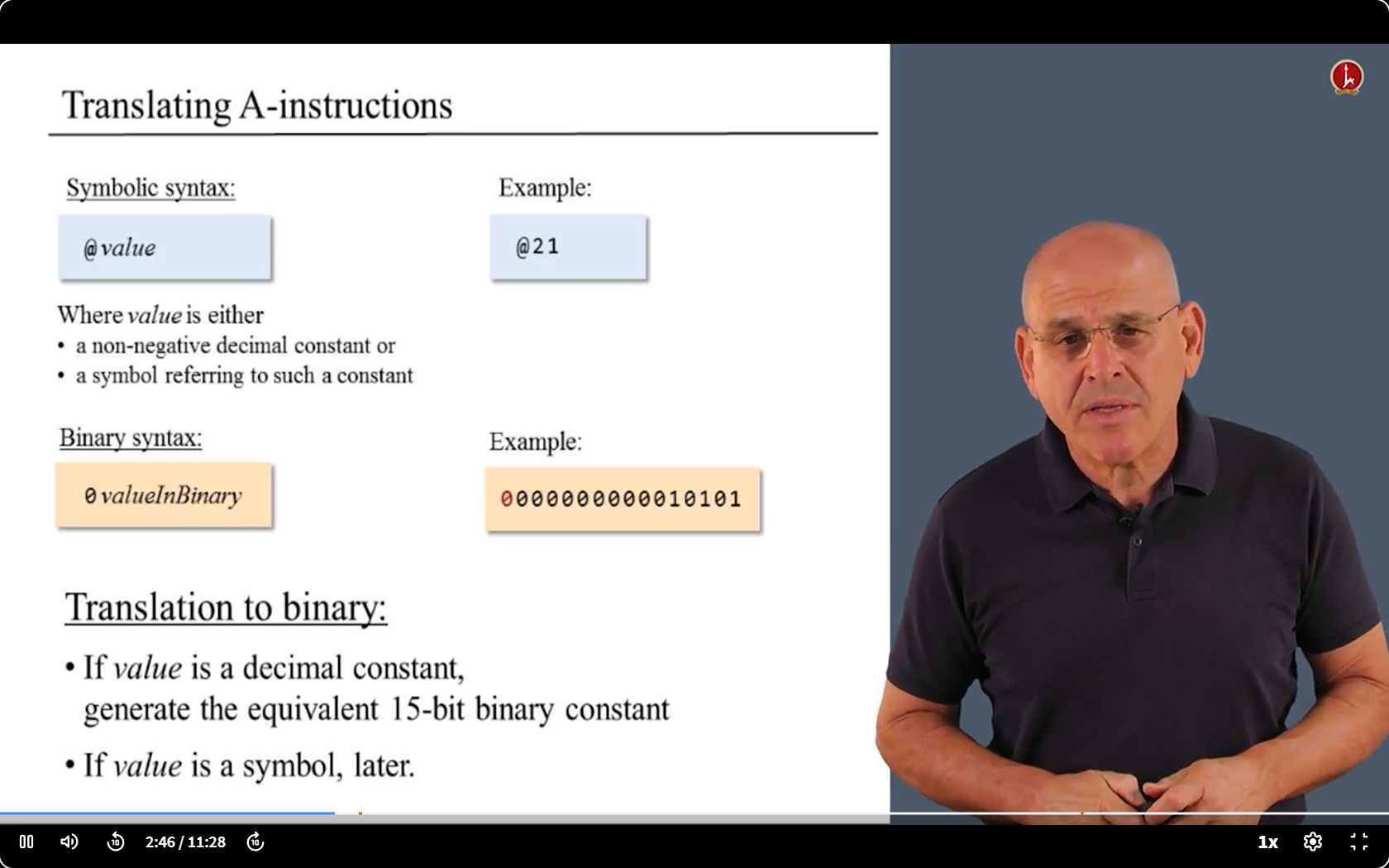
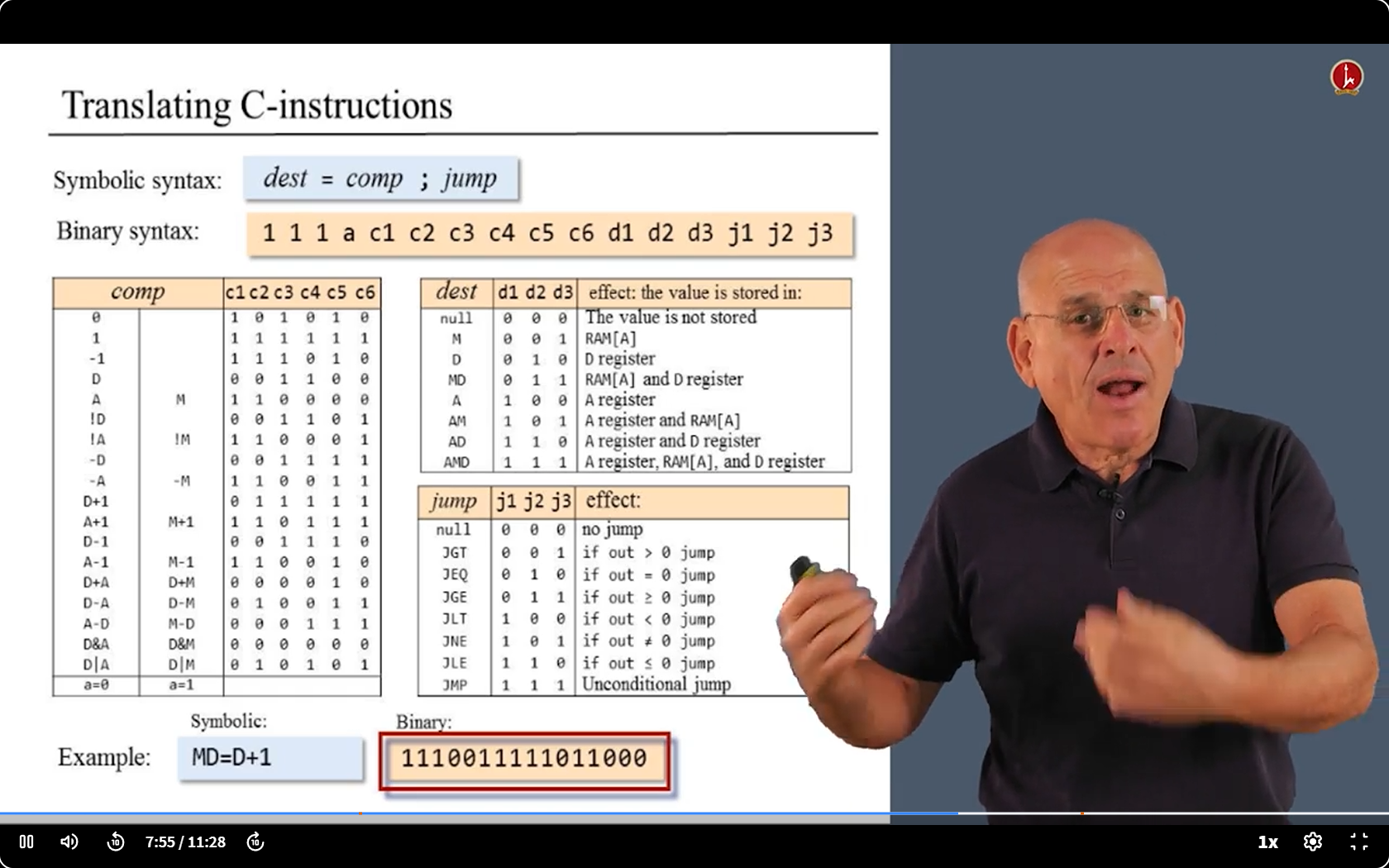
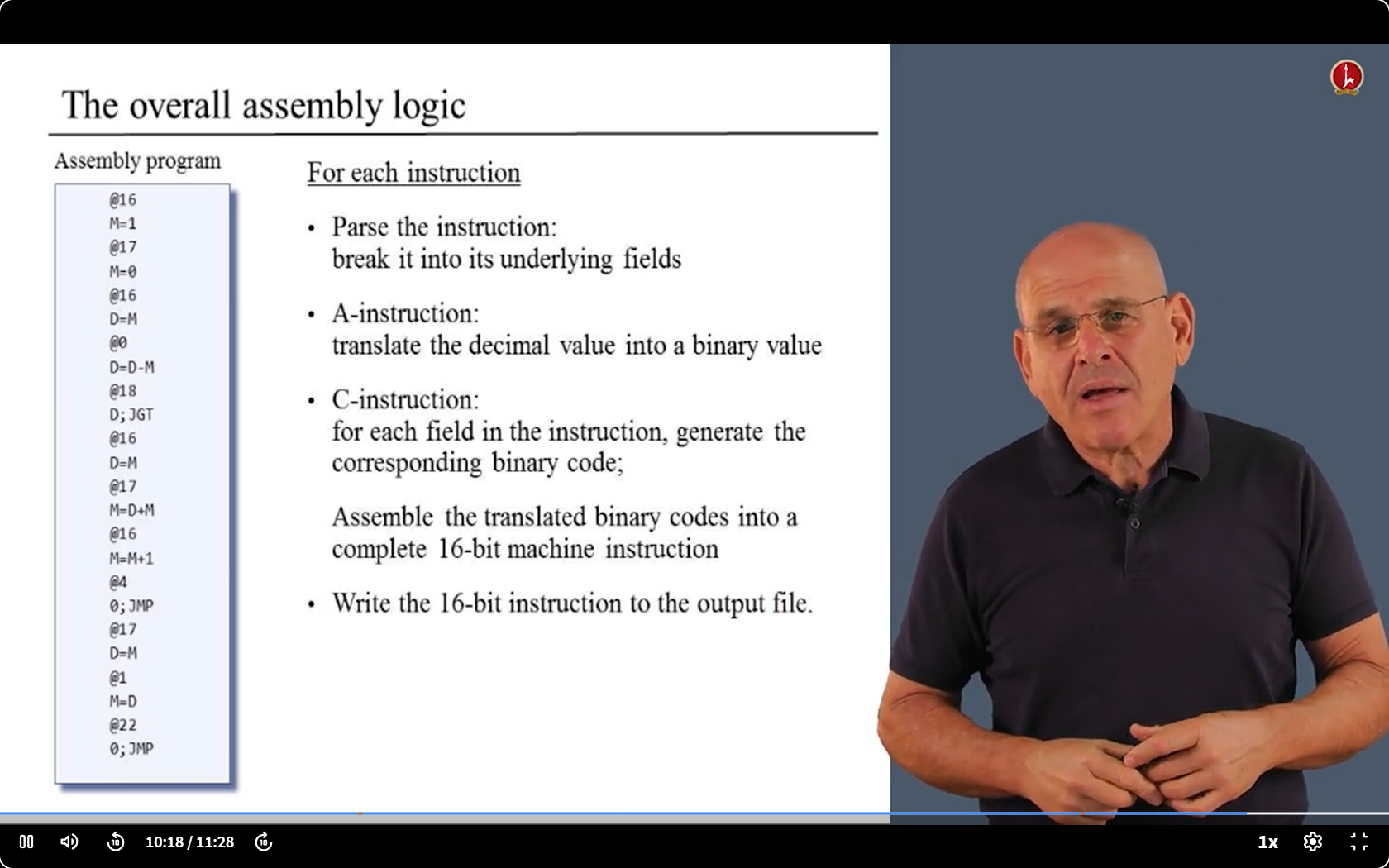
6.4 Translating challenge 1 : Struction with Symbols


6.5 Use Java to build Assembler
三个步骤
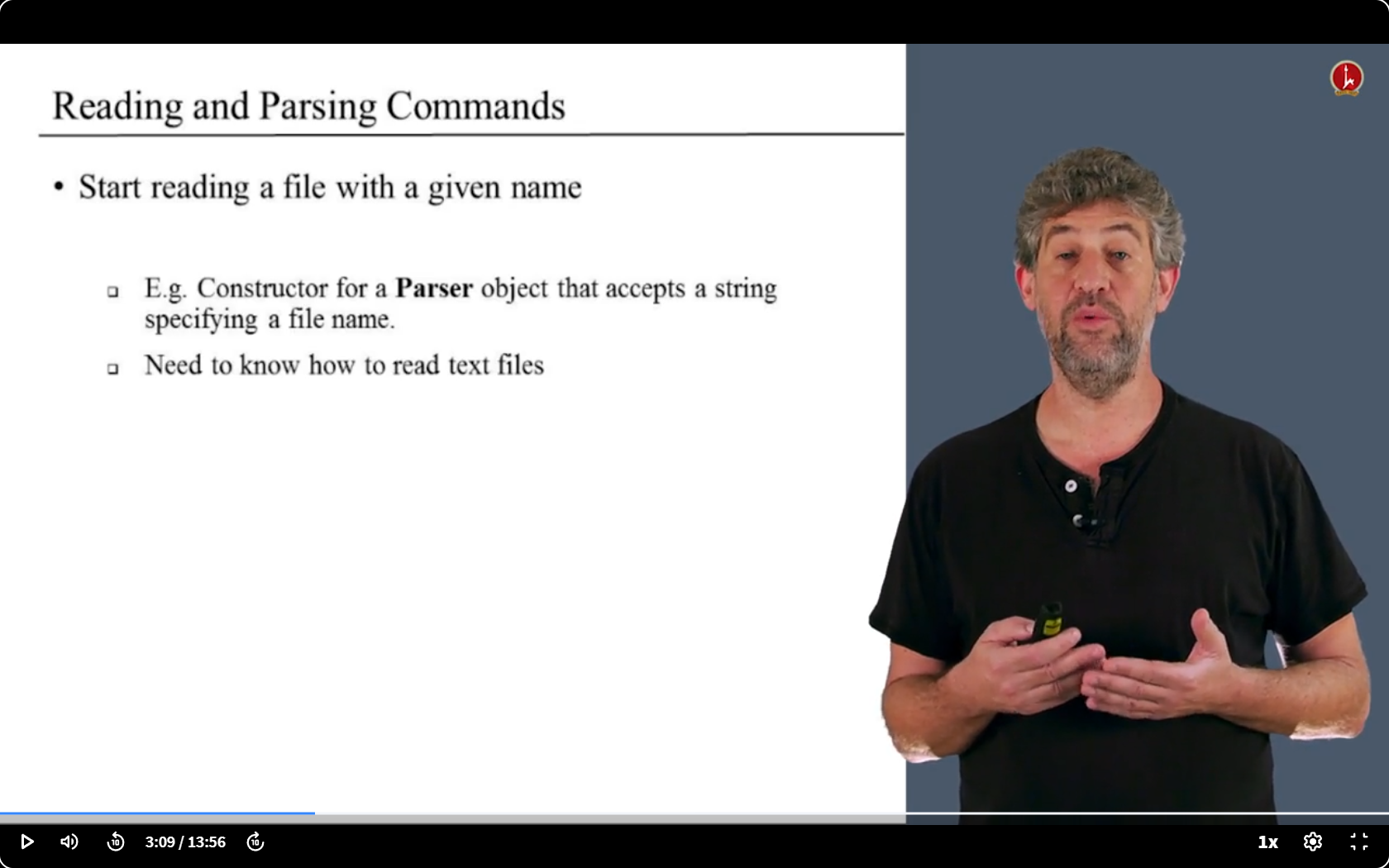
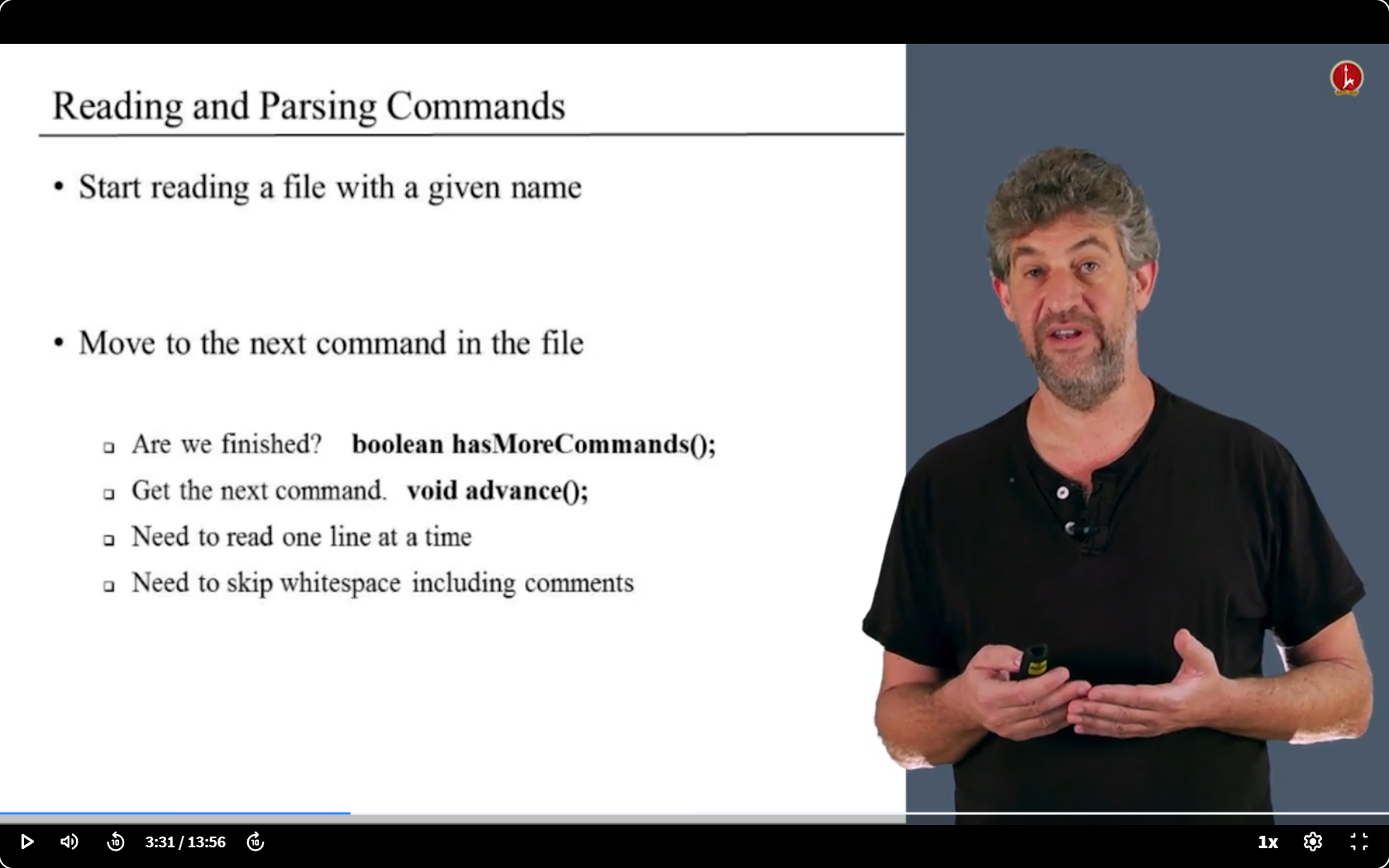
- 第一步:解析命令
- 读取文件一个个获取命令,看是什么命令
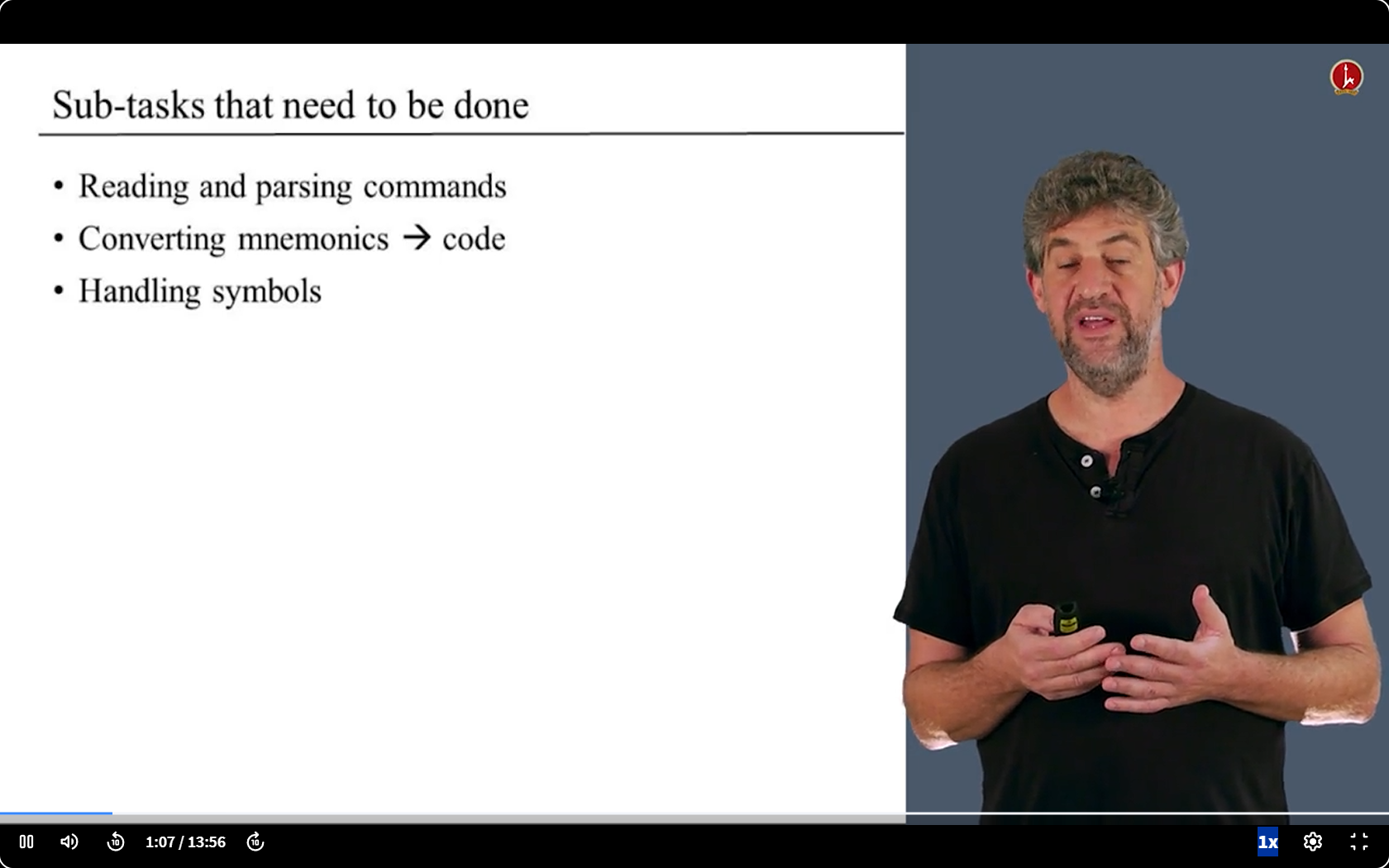
- 第二步:
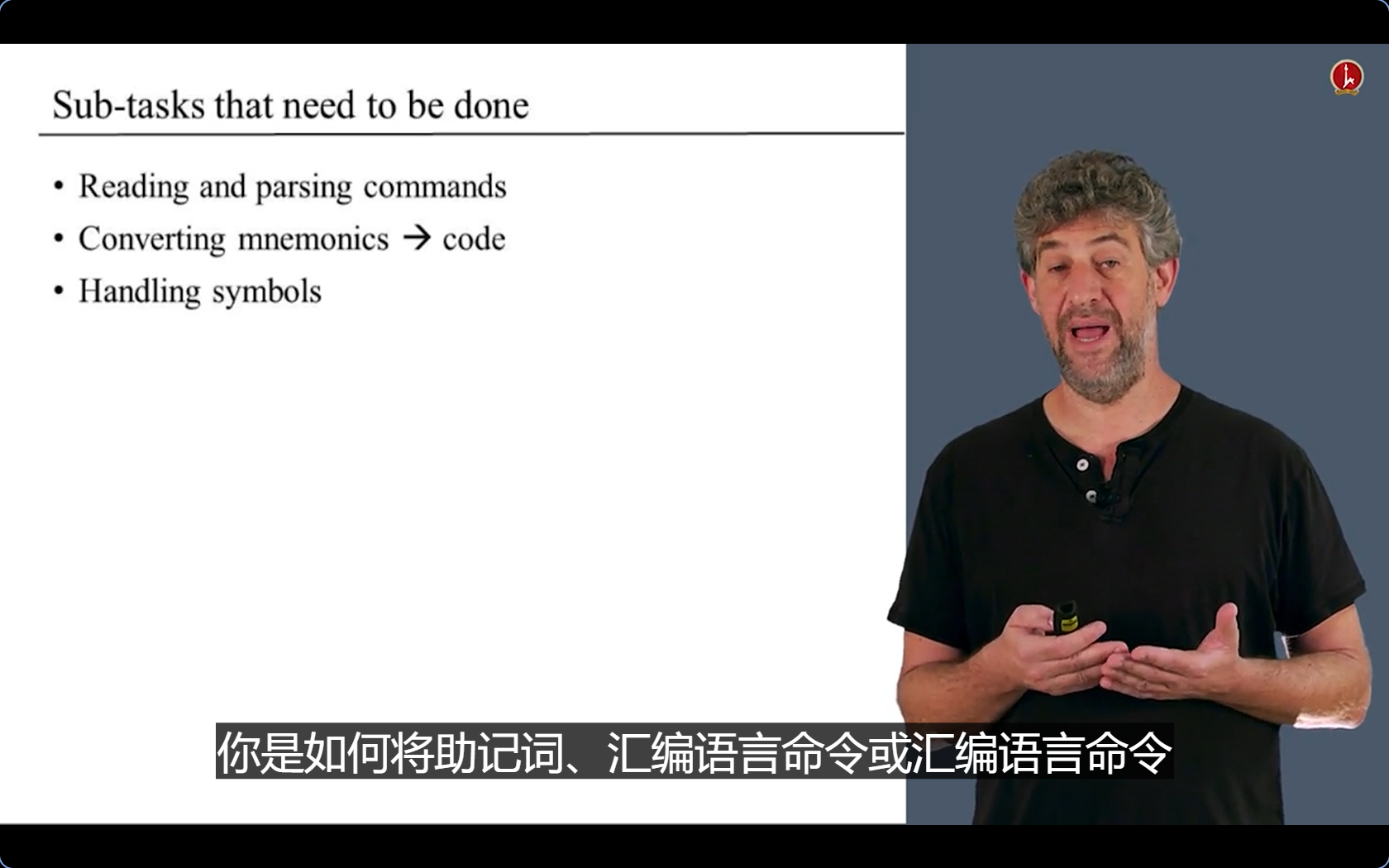
- 第三步:处理符号
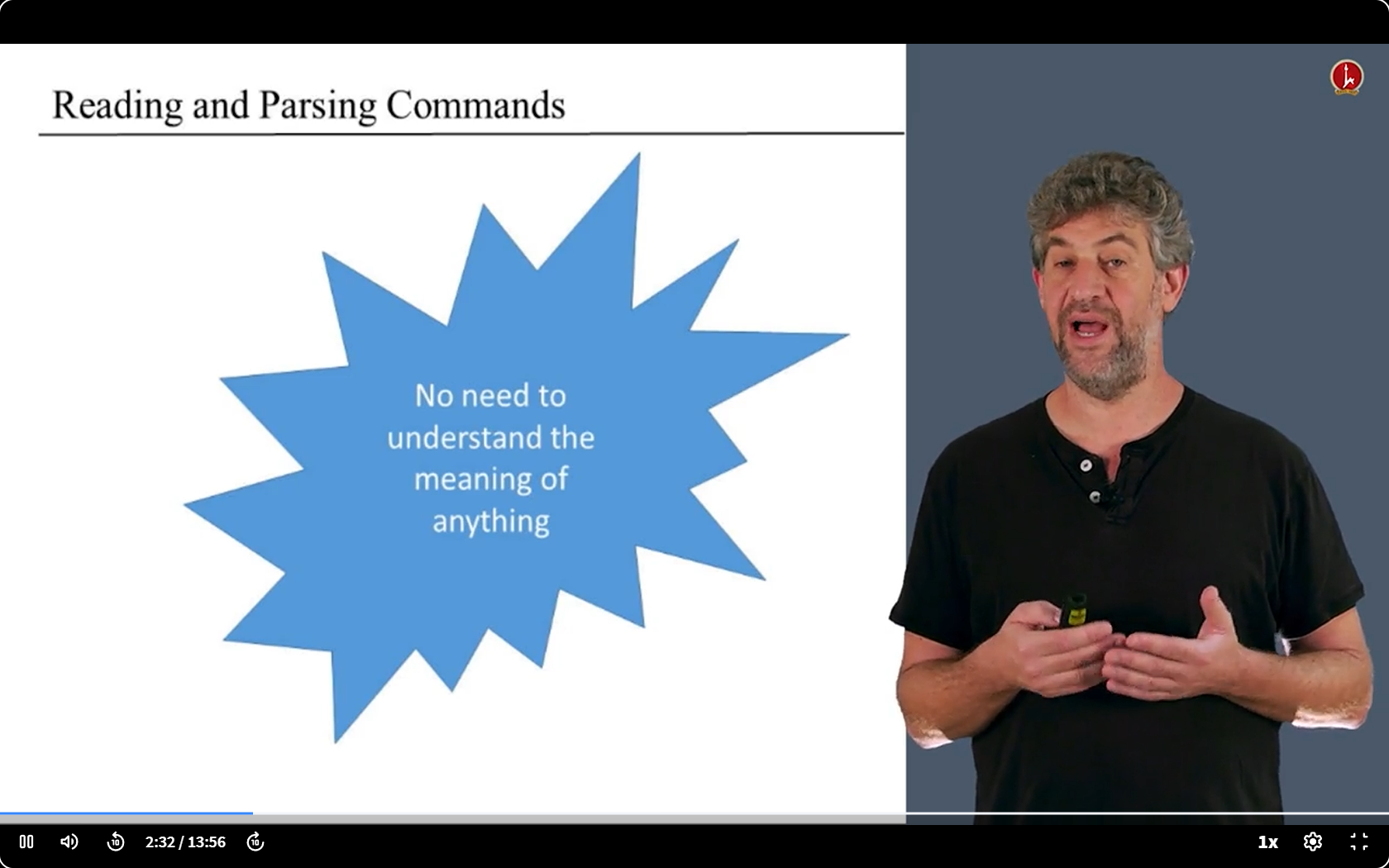
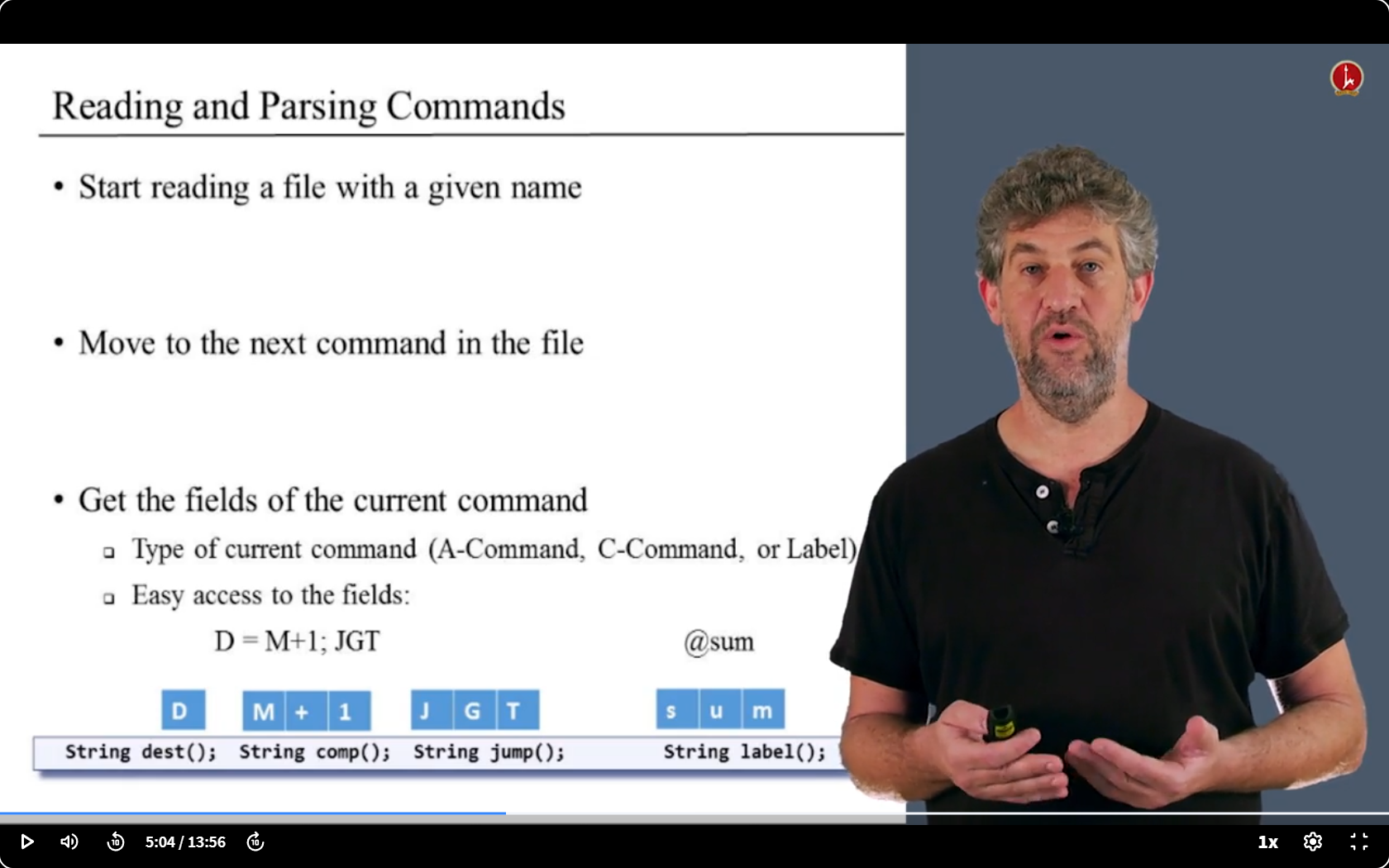
第一步
- 唯一需要了解的就是输入语言的格式,以及它如何分解成不同的组件
第二步

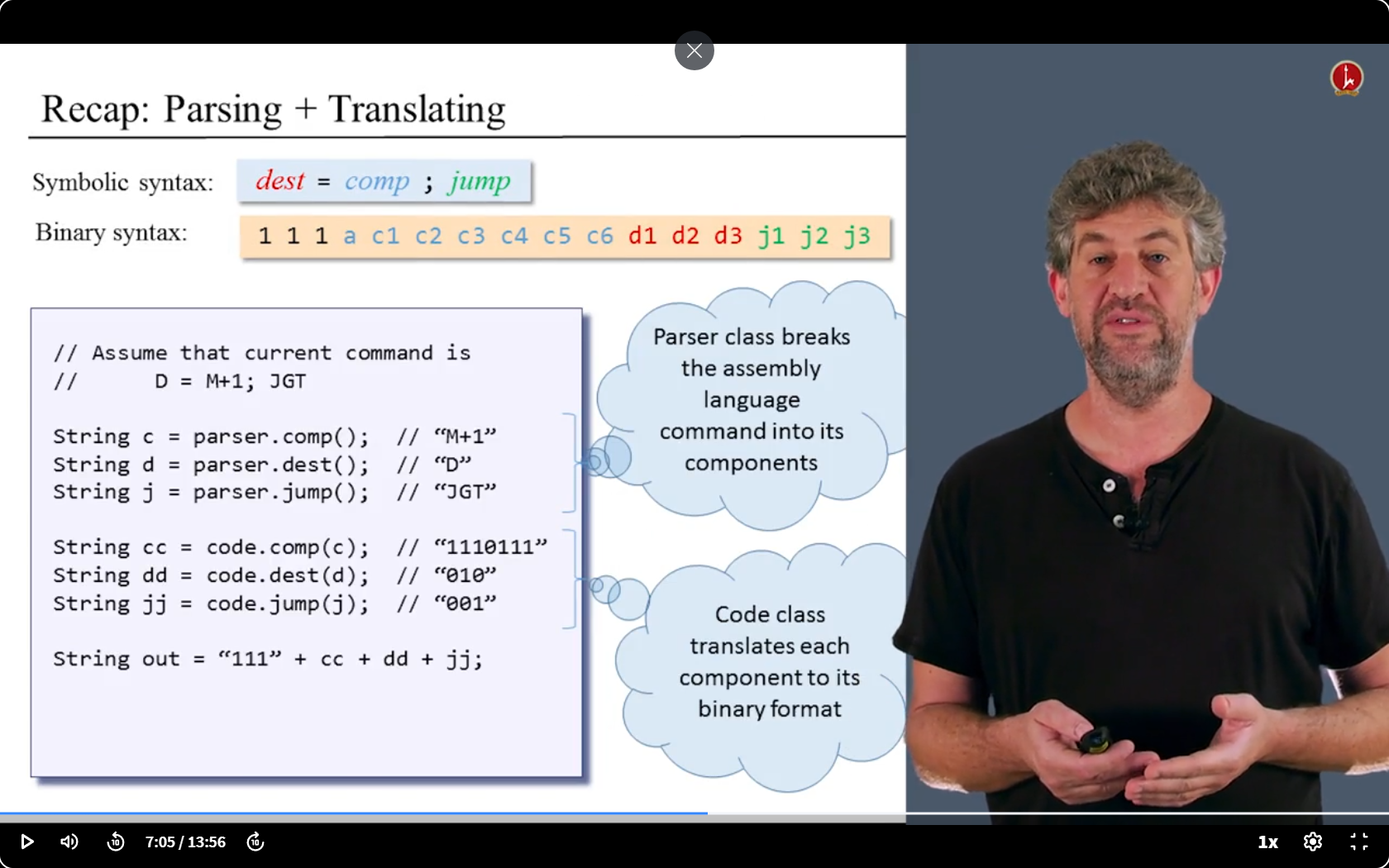
第三步
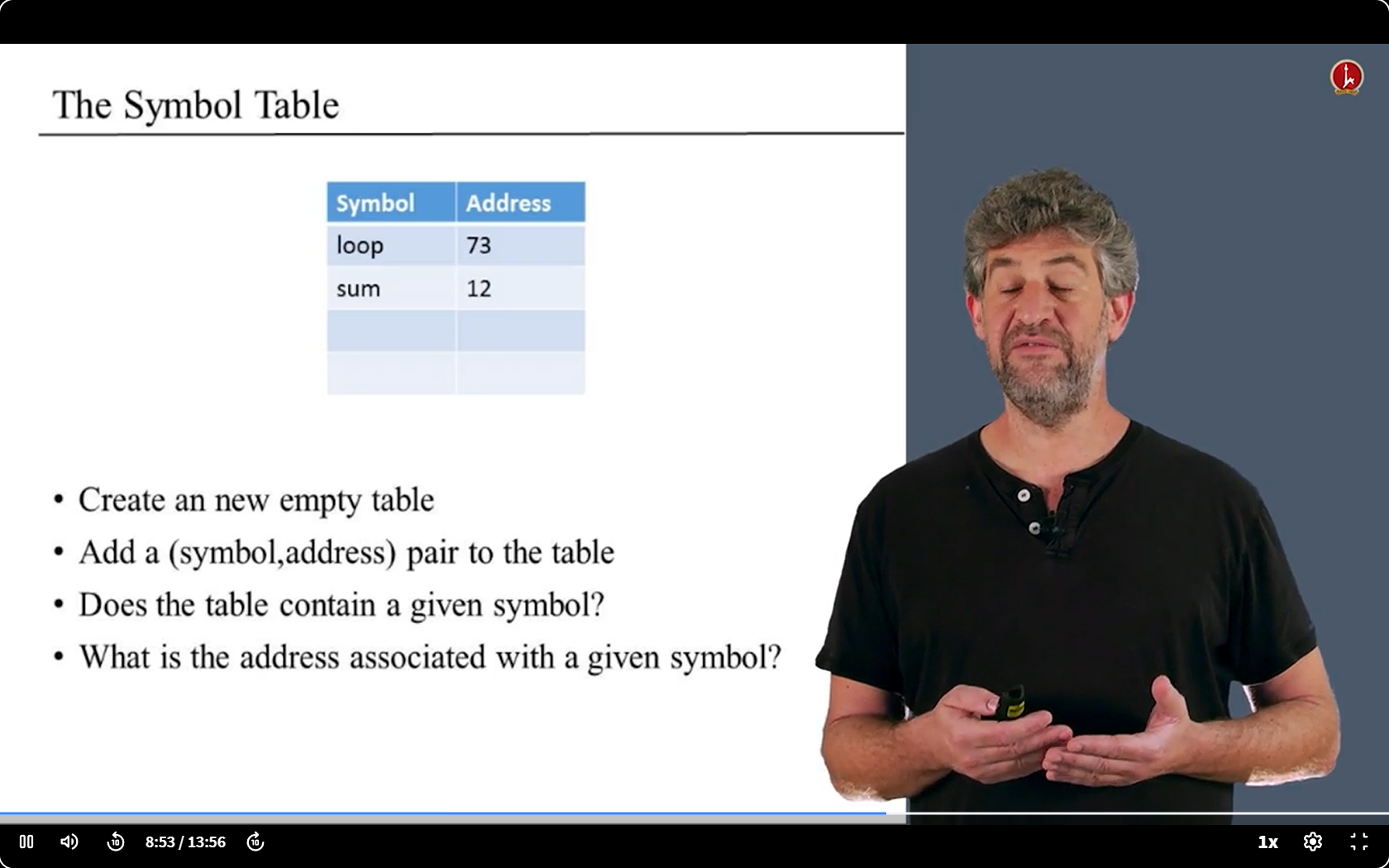
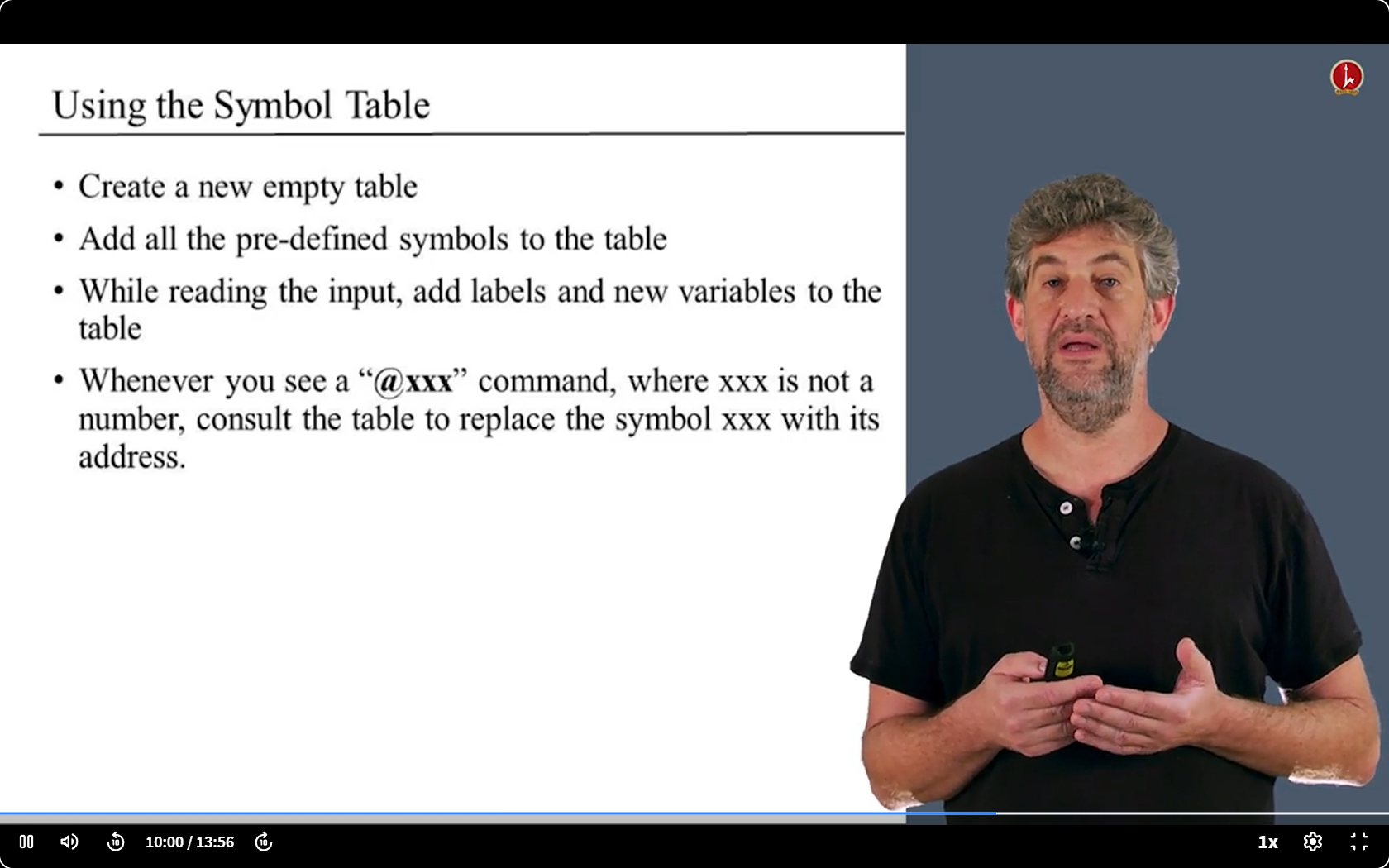
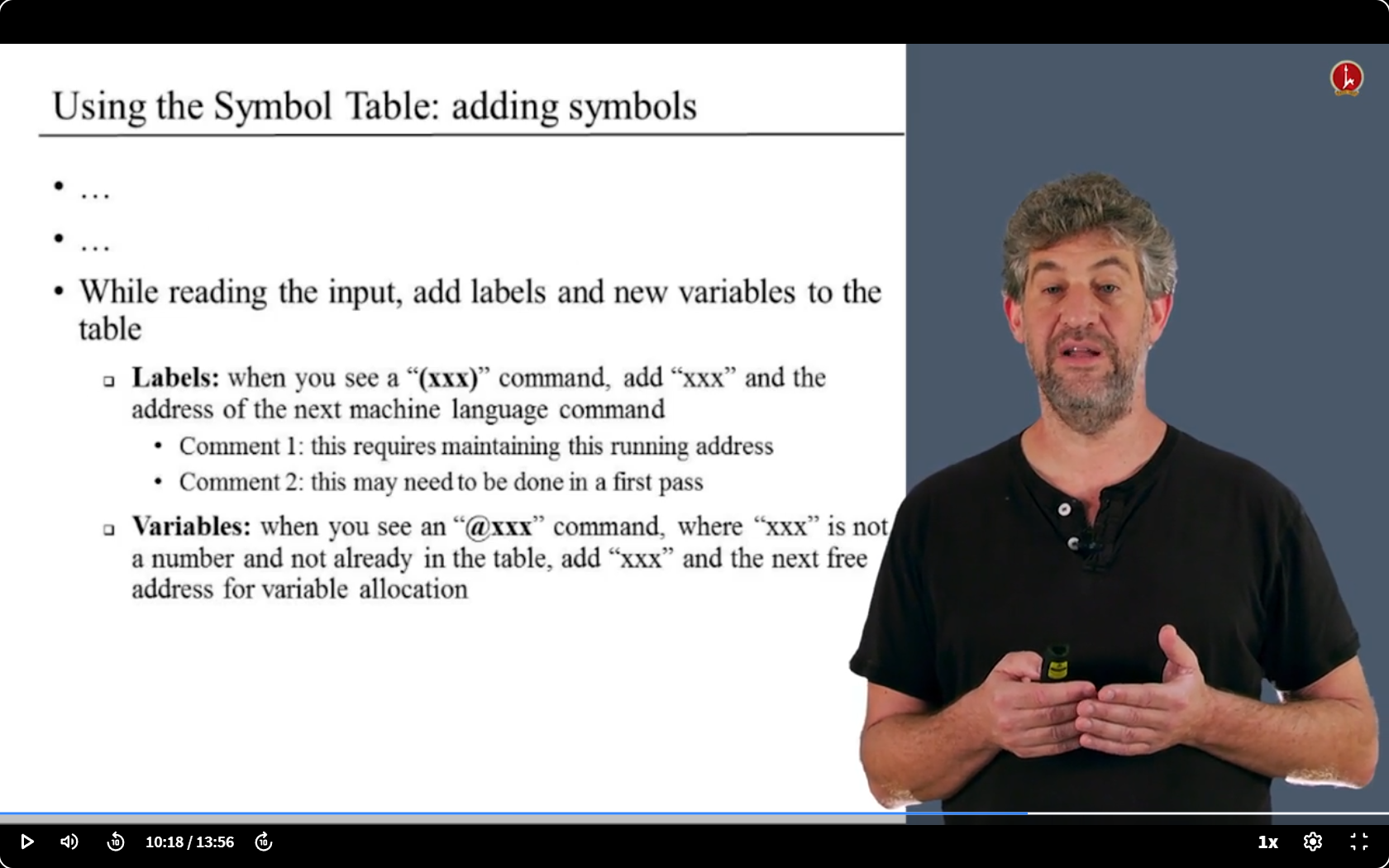
- 唯一要做的:保存符号和内存地址之间的关联
总的来说
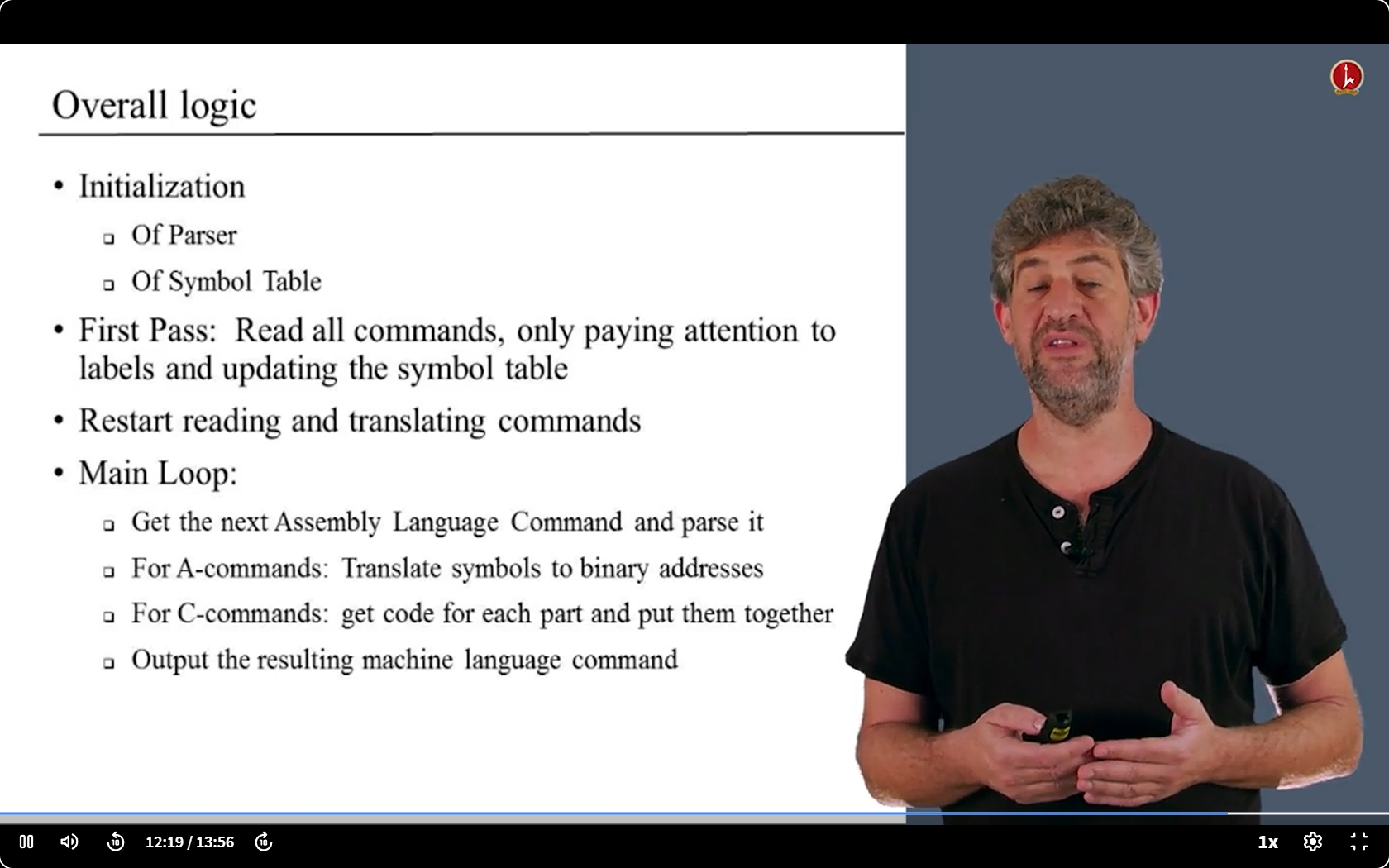
6.6 Proj 6 Overview
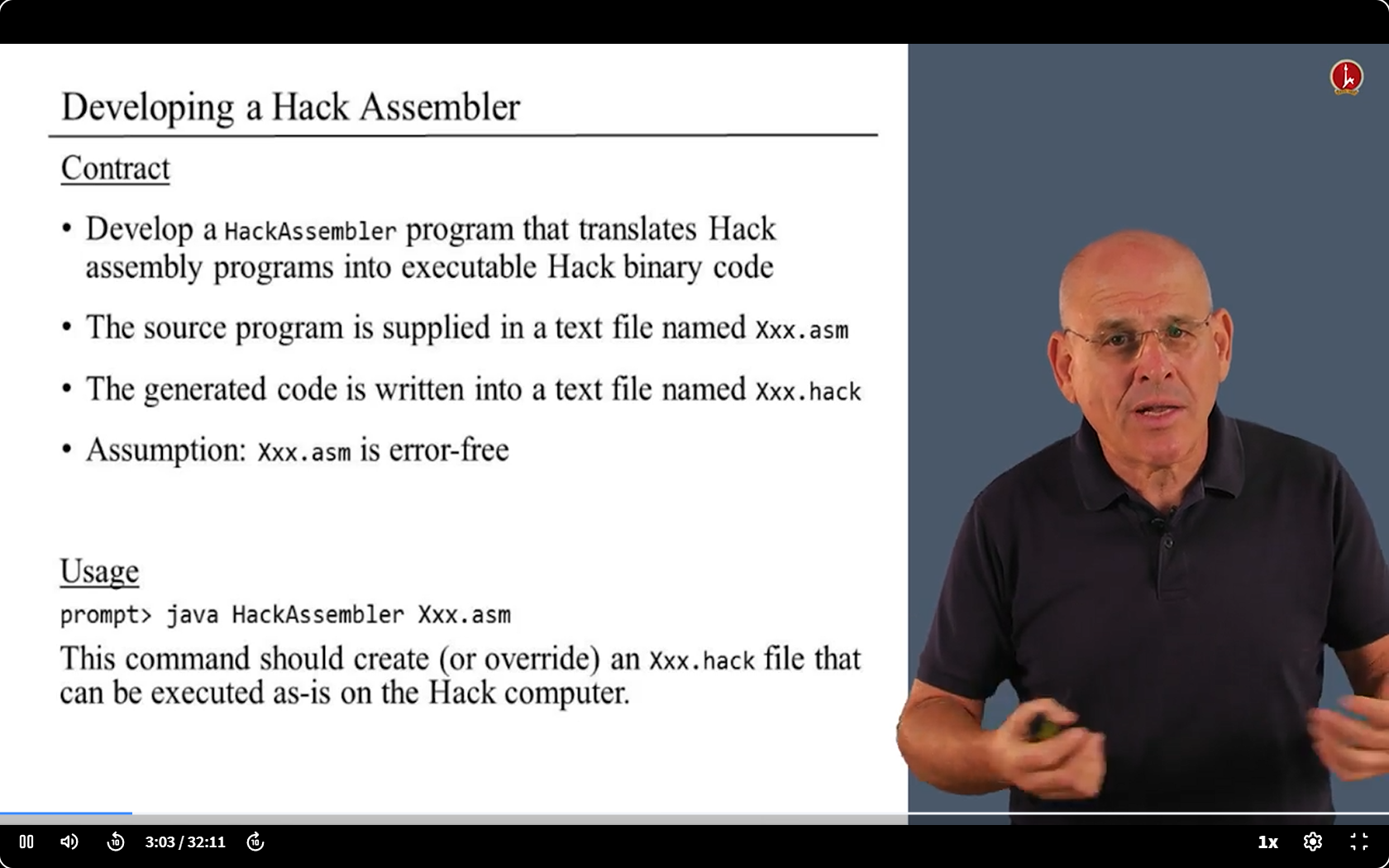
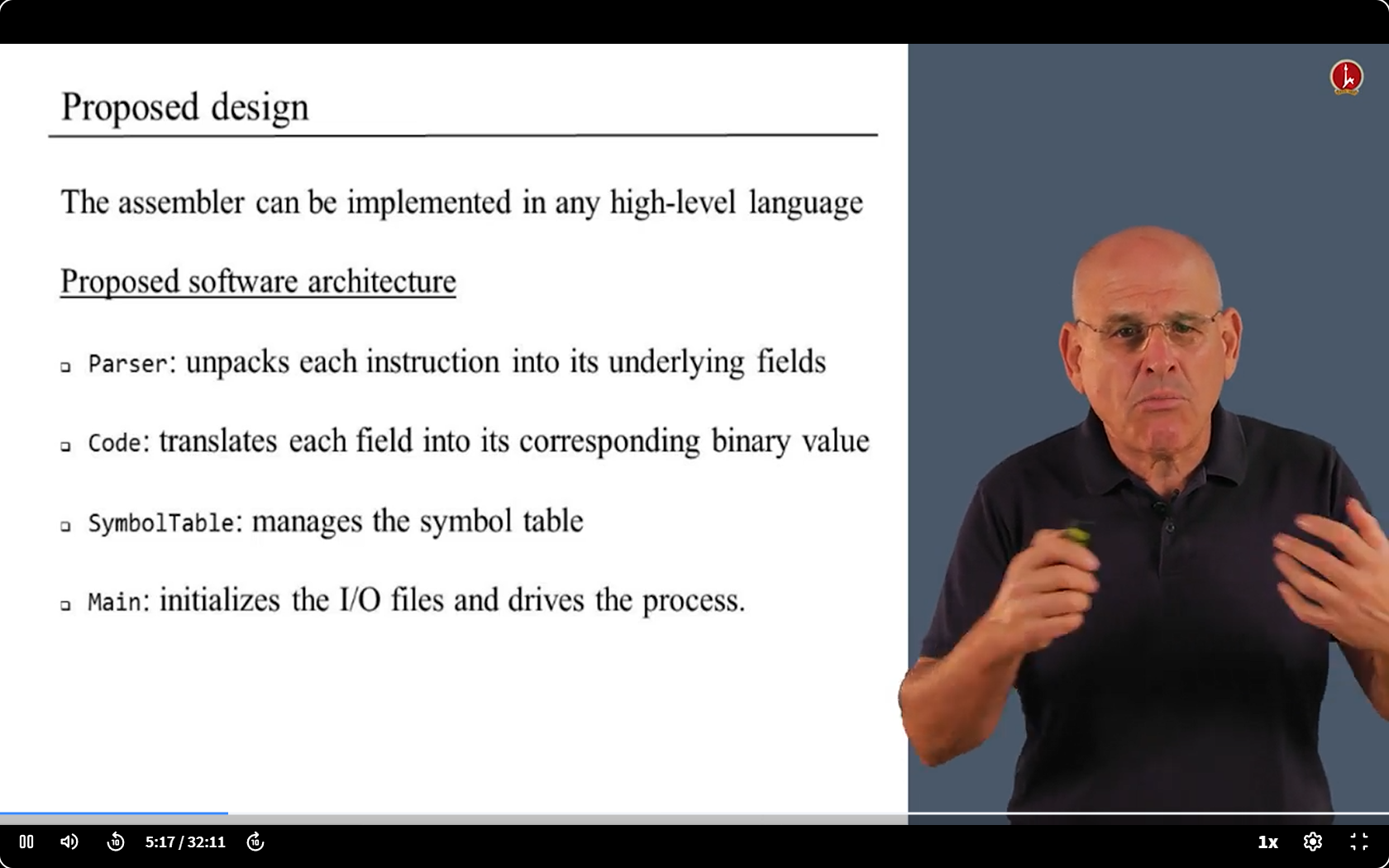
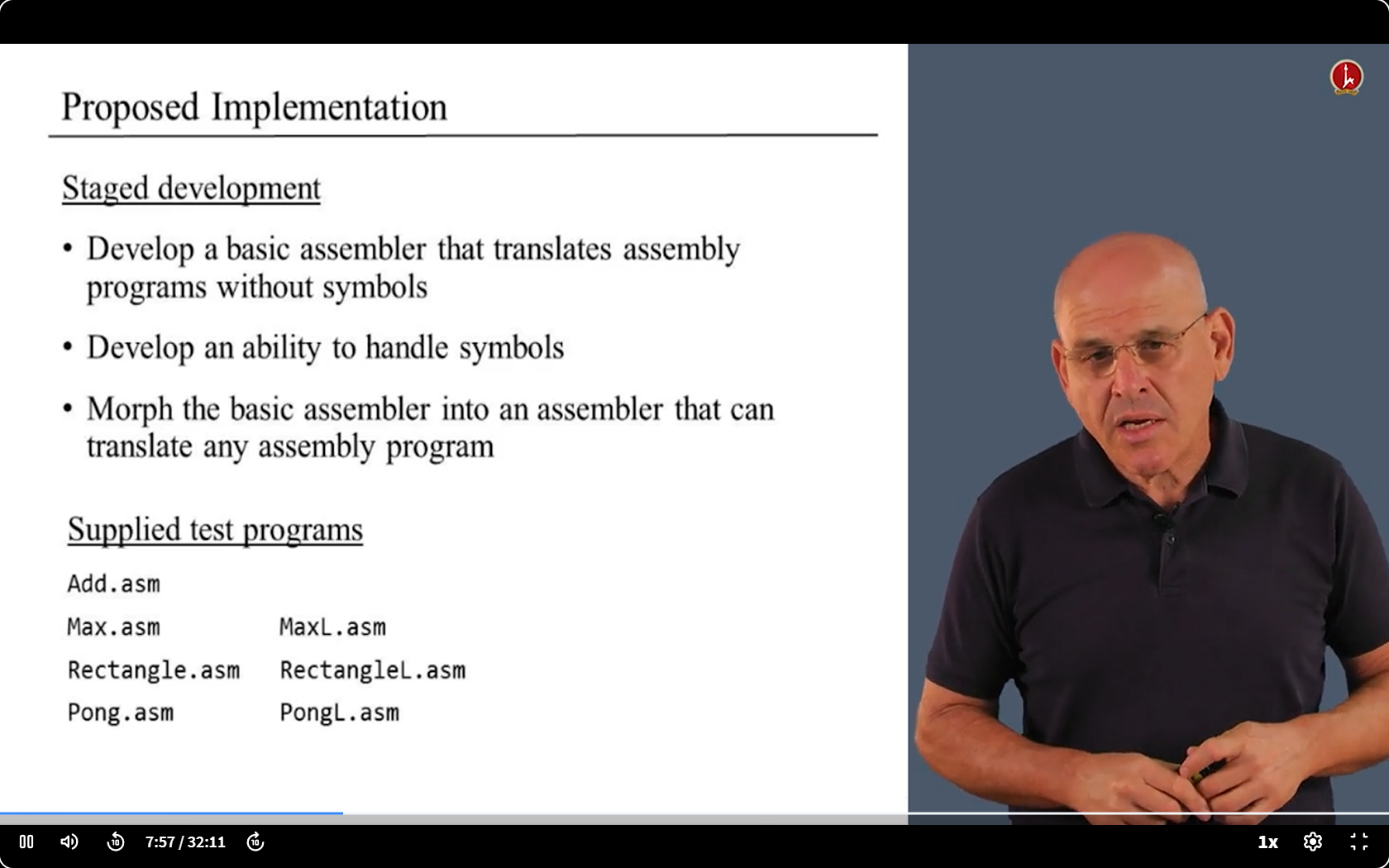
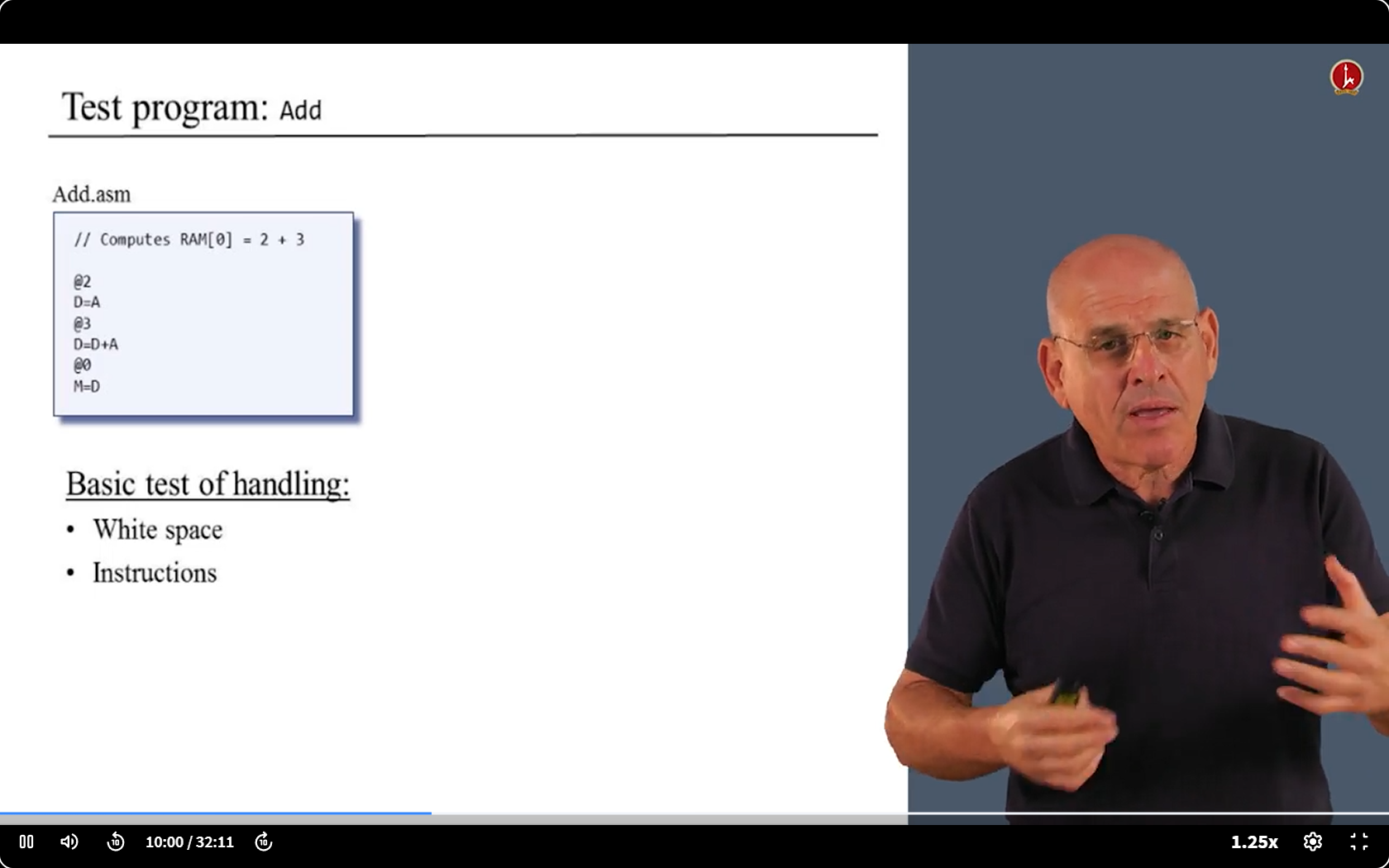
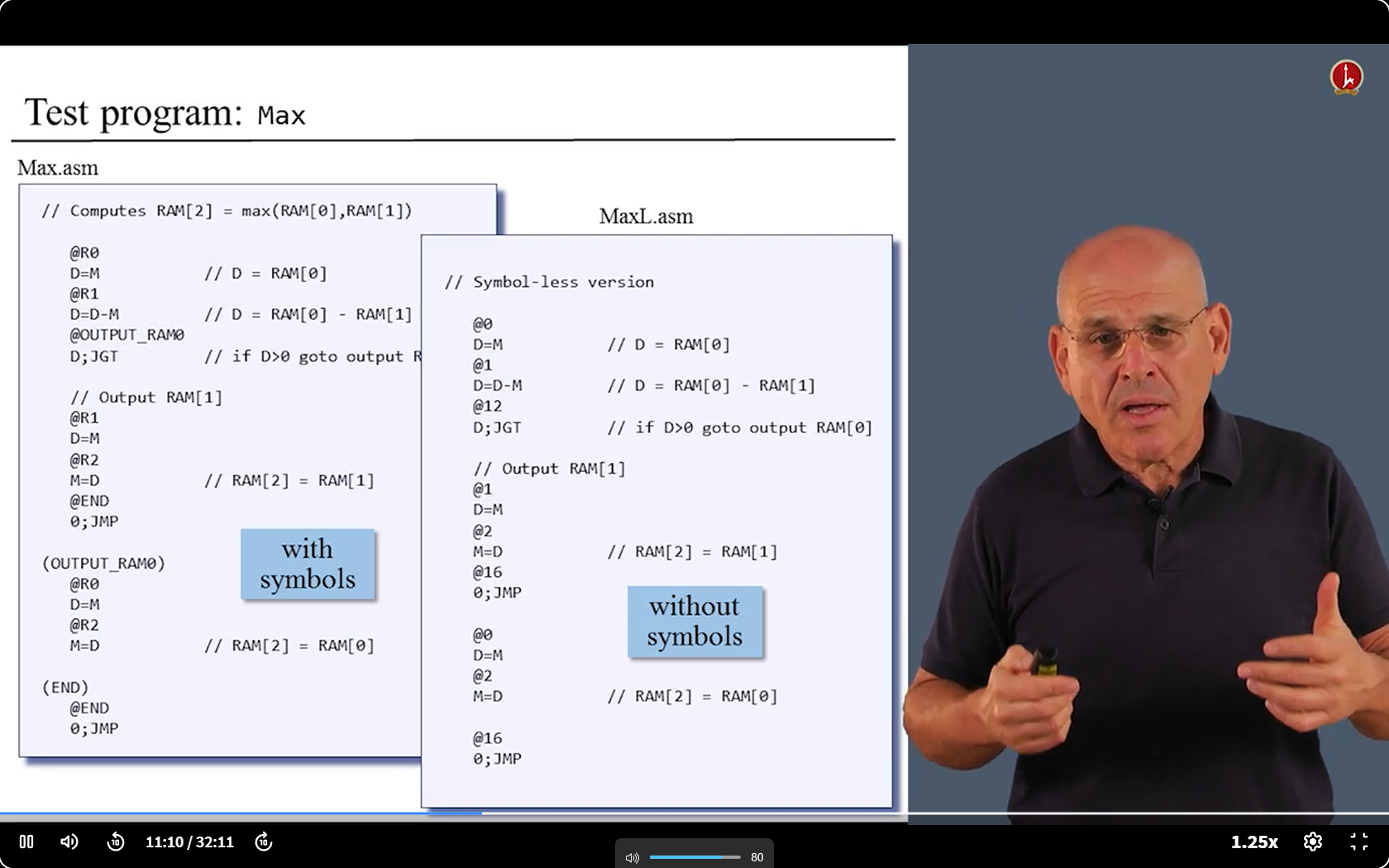
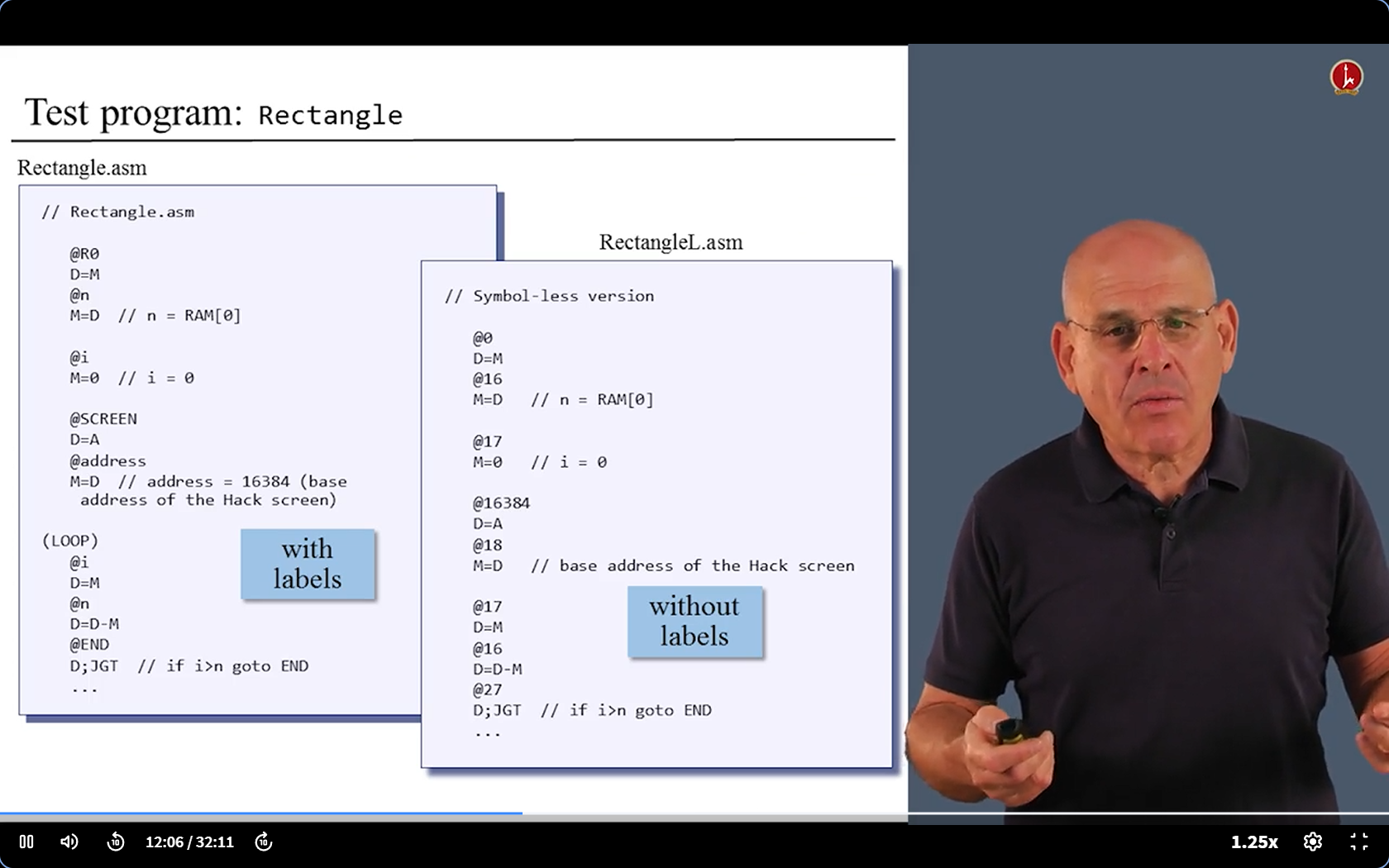


6.7 code
Parser
1 | class Parser: |
Code

1 | class Code: |
SymbolTable
1 | class SymbolTable: |
Assembler
1 | import os |
main
1 | # 1.导入模块 |
评论